
Bryan Stetser, owner of Computers & More located at 800 S. 2nd Street, in Raton will be providing hints and tips for care and use of your computer or laptop on this page. His shop hours are: 9:00 AM – 2:00 PM Thursday and Friday. Questions or need help? Call Bryan at (505) 990-0128.
Not only does Bryan provide basic PC service and repairs, specializing in software related issues, but he also has some laptops and computer parts, hard drives, and other supplies on hand.
Select from the list below for helpful tech advice:
- Skype Shuts Down For Good
The Ongoing Battle Against Ads - FREE Scam Detection Software
- Movies Anywhere Library Service
- Will the New Tariff Cause Electronics Pricing to Go Up?
- Obsolescence in Technology
- BITLOCKER Bug
- Gaming News: Nintendo Announces Switch 2 Release
- Google Chrome Browser Extensions
- Is TikTok’s Time Up?
- Arcade-Style Game Controllers
- Merry Christmas From Tech Time
- Testing Storage Devices Purchased from Temu
- Portable Software for PCs
- Is My Computer Safe During a Geomagnetic Storm
- Microsoft Hello for Windows 10/11
- WE ARE MOVING!
- Windows 11 Recall Feature
- Kaspersky Migrates Users After US Ban
- Windows File Explorer Preview Pane
- Should You Defrag Your Drive?
- Disposing of E-Waste
Ethernet vs Wi-Fi - Kaspersky AV Banned in United States
- BITLOCKER for Data Encryption
Crowdstrike Outage - My Amazon Prime Day Picks
- Passkeys
- We Almost Had a Winner …
- Contest Time
- Artificial Intelligence
- Just For Fun
- Getting Started Creating a Smart Home
- How Smart is Your Home?
- Make Web Browsing a Breeze
- REVIEW: Portable Wireless Thermal Printers
- What’s In Those NFC Tags and How Do They Work?
- What is NFC?
- How to Take Screenshots on Your PC
- Does Your Desktop Computer Need a Maid
- Does Your Laptop Need a Maid?
- PC Keyboard Shortcuts to Speed Up Your Productivity
- Paypal Scam
- What are those F Keys For, Anyway?
- What are Those F Keys for ,Anyway? PART 2
- What are Those F Keys for, Anyway? PART 3
- Google Docs Phishing Scam
- Remote Access Software
- Virtual Private Networks
- Free Productivity Software
- What is RAM?
- How to Choose a Flash Drive for Data Storage
- Facebook Video Scams
- Is Your Internet Fast Enough?
- Is Your Computer Fast Enough?
- Put Some Pep in Your Computer’s Step
- Beware – Hackers Pretend to be a Friend Asking for Help
- The Importance of Surge Protectors
- Windows Security Pop Up Scam Ad
- Windows 11 and the Future of Computers
Skype Shuts Down For Good
Posted March 3, 2025
by Bryan Stetser

While there are currently plenty of applications which allow you to talk to others online, Skype was a rather popular application back in the day and possibly the first one you ever used if you were into video calls. A VoIP service (voice over IP), it was released over 23 years ago back on August 29, 2003. Skype allowed you to create an account and communicate with others via voice calls, group chats, video conferences, and was useful for businesses or if you had an online friend you wanted to talk with.
Its relevancy began dwindling over time as as other competing VoIP services came out over the next few years such as Discord, WhatsApp, Messenger, and many more.Microsoft ended up buying out the Skype Communications company in 2011 for over $8.5 billion. With all this and the dwindling popularity of Skype, it comes as no surprise that Microsoft announced they are killing off the service starting on May 5th of this year.
If you by chance still have or know someone who has a Skype account, Microsoft is kind enough to let you choose between two options on what you want to do with your account.
- If you decide to sign into Microsoft Teams (Microsoft’s team application service that has similar functionalities to Skype and is a part of the 365 line of applications), it will sync your chat messages and contacts so business can continue as normal, as well as being able to chat with other Skype users until the service eventually goes down.
- If you have no interest in Microsoft Teams though, you can export your data such as call history, chat messages, and contacts, so you can keep an archive of your data while you move to greener pastures.
If you have a Skype account and need help migrating things elsewhere, come on down to Computers & More of Raton and we can help you. We are located at 800 S 2nd Street and our hours are Thursday and Friday 9:00am – 2:00pm.
The Ongoing Battle Against Ads
Posted February 27, 2025
by Bryan Stetser

If you’ve been keeping up with adblocker news recently, you may have heard about Google’s increasing attempts at snuffing out adblocking software (extensions) on their browser, Google Chrome. As of recently Ublock Origin, a popular and widely used adblock extension for the Chrome browser has finally been killed off as Google enacts their push for extensions to use Manifest V3 (a set of rules and restrictions for browser extensions).
If you happen to be using Ublock Origin or are worried about how intrusive and dangerous ads are across the internet, then allow me to suggest some alternative options.
Adblock Plus is a decently popular option for dealing with ads online and has been around for over 20 years featuring the usual options such as a whitelist to allow ads on certain sites, subscribing to lists of commonly blocked public domains, blocking advertising cookies and other trackers lurking in the background as well as being Manifest V3 compliant.
Adguard is also another good option, as well as Ghostery. The former has a system in place to stop connections to malicious/dangerous domains or sites and can properly collapse and handle removing ads. The latter is also good at blocking tracking and handling privacy, but unlike Adguard which only has Manifest V3 support in beta, Ghostery is already compliant as of version 10.
If you would still prefer sticking with the Ublock brand, you could try out Ublock Origin Lite which is similar to regular Ublock Origin, but might lack certain functionality as a consequence of being Manifest V3 compliant.
Alternatively if you don’t care about moving to a different ad blocker, you could switch to a different browser like Mozilla Firefox or Microsoft Edge. Firefox has no current plans to drop support for Manifest V2 (meaning you can still use regular Ublock Origin if you desire) and Edge still seems to allow Ublock Origin to work without problems (for now at least).
If you would like more help moving to a different adblock or a different web browser, visit Computers & More of Raton at 800 S 2nd Street and we’ll be happy to help. Our hours are Thursday and Friday, 9:00am – 2:00pm.
FREE Scam Detection Software
Posted February 21, 2025
by Bryan Stetser

This article is not paid for or sponsored by Seraph Secure.
You probably already know how easy it can be to fall prey to online scams and these scams take on many variations and forms, often made to steal your information or money, oftentimes both.
If you, a family member or someone you know has fallen victim to a scam, you know it can be absolutely devastating. Money scams carry the very real potential to financially ruin an unsuspecting individual. These scams are virtually all based out of India, and start with a phone call, text message or email. Some of the more popular ones are offerings of refunds for a renewed subscription or an expensive order you don’t recall placing. Others start with a communication about a company being unable to deliver a parcel.
Scammers are extremely skilled in vetting those who likely will be a suitable victim within the first few minutes of a call, targeting those who aren’t particularly computer savvy, especially the elderly.
Seraph Secure was created by Kitboga, a well known YouTuber who has spent years dealing with scammers. His mission has been to not only spread awareness by exposing phone scammers, but also devoting hours (sometimes days, weeks and months) to engaging scammers, which is referred to as scam baiting. By keeping scammers busy, that prevents them from scamming someone else.
Kitboga’s scam detection software is easy to use, runs fast, and is lightweight enough to keep running in the background. It also helps by blocking potentially malicious websites, as well as protecting against and removing unauthorized remote access software that scammers might try to install on your computer. It can also be set up to monitor other devices from your friends or family members, receiving text and email messages if Seraph Secure detects something fishy is going on.
While you can use it for free on a device without making an account if you need an application to help remove existing scam threats and block remote connection software, if you or a loved one need more than that, you can pay $4 a month to get some extra features to stay safe, such as scam site detection, new website domain warnings, typo protection (helps against scammers that intentionally misspell a websites name to trick you) and deceptive utility warnings for when scammers try to misuse command line utilities like Netstat to pull up technical network data as a scare tactic. If you are willing to pay $14 a month, you can set up Seraph Secure across up to 10 devices for multiple family members. If you aren’t sure whether or not it’s worth paying for, there’s a 14 day free trial that lets you test out the software before you commit to paying. If you are interested in trying out this software for yourself or a family member, feel free to check the link below.
Note: This application is currently only available for Windows 10/11, support for MacOS and IOS/Android is coming soon. This is not an AntiVirus program, but strictly for scam detection.
Seraph Secure – Anti Scam Protection for Online Scams
Click here to visit Kitboga’s YOUTUBE channel. He has tons of scam baiting videos to watch, learn and be entertained by.
Movies Anywhere Library Service
Posted February 15, 2025
by Bryan Stetser

Note: This article is not sponsored by Movies Anywhere or any of the movie companies involved in the program.
It’s pretty safe to assume just about everyone has a collection of movies they enjoy watching. Some might prefer to watch them physically on a DVD or Blu-Ray player while others might watch them on streaming services like Amazon or AppleTV. One problem that can come about, especially with large collections is keeping everything organized. One person might have their collection on a single platform, while others might have movies split up across multiple platforms, therefore requiring logging in to different services to access them.
If you’ve been struggling to keep your digital collection organized and want an easy way to access movies no matter where you purchased them from, it might be a good time to consider looking into using Movies Anywhere.
Founded by the Walt Disney Company and launched on February 25, 2014, Movies Anywhere is a cloud-based movie library service that syncs any compatible digital movies you own across the services you use. For example, I had an old digital copy of Marvel’s “The Avengers” I had purchased many years ago on iTunes, and it was extremely easy to sync up to Movies Anywhere and the movie was ready to watch instantly, with the added benefit of making it available to watch through my other platforms as well. Meaning I no longer had to log into iTunes (now AppleTV) to watch it; the movie shows up on my YouTube and Amazon account libraries as well.
There are a few caveats though, as not every movie is compatible with the program (it mainly supports titles from Disney, Sony, Warner Bros, and Universal). Movies Anywhere also only supports movies (So no TV shows for example), and you do have to be a US resident to make an account (though you can access it outside of the US once make your account)
Even if you don’t tend to purchase many digital movies, keep Movies Anywhere in mind as certain streaming platforms can offer up movies at discounted prices or sometimes even for free. Doing a search for movies through Movies Anywhere will pull up pricing and deals from all the platforms it supports making comparison shopping a breeze. You’ll be able to see the best pricing all in one place, rather than having to search each platform individually.
Certain physical copies (DVDs and Blu Ray) of compatible movies may also have an included code for an add-on digital copy. This not only allows you to have a physical copy, but you’ll also be able to watch it digitally if you want.
If you use more than one digital streaming platform and have digital movie purchases scattered around, try out Movies Anywhere to keep your collection in one place. Best of all, Movies Anywhere is free – no extra fees or subscriptions needed.

Will the New Tariff Cause Electronics Pricing to Go Up?
Posted February 8, 2025
by Bryan Stetser

You may or may not have heard already, but it seems like pricing of certain electronics will likely be going up this year. As of February 4, 2025, President Donald Trump decided to impose a set of tariffs on Chinese goods at 10% across the board. If you aren’t sure what the word tariff means, it’s a term for taxed goods that are either imported or exported out of a country. Considering that many electronics such as computers, consoles, phones, and parts are most often produced and imported from China, it means we will likely see these items cost more this year unless something changes down the line. If there are any devices in particular that you have had your eye on this year, this might be worth taking into consideration seeing if your purchase will be affected by this and budget accordingly.
On a side note, if you are looking for a good laptop for work, school, or general internet browsing-related tasks, we have limited stock at Computers & More of Raton. Reasonably priced at $249.99, these laptop are a good choice for most users. They are not designed for high-end tasks such as video rendering, but they do serve nicely for most anything else. We offer free setup as well if you need help with that.
Once we run out, we will unfortunately not be keeping laptops as regular stock, though if you need help purchasing a new one, we will be happy to help guide you to the right device. We will still carry our regular stock of accessories and micro SD cards for your storage needs. Come on down to 800 S 2nd St or give us a call at 505-990-0128, we are open on Thursdays and Fridays 9 AM to 2 PM and have a great weekend!

Obsolescence in Technology
Posted February 1, 2025
by Bryan Stetser
It is always consistent that computer hardware and technology will keep advancing and improving as time moves forward. A computer that you buy today will become instantly obsolete as soon as the next batch of devices get announced.
While you may feel tempted to buy the latest thing, whether it be a new PC, a GPU (Like the new Nvidia RTX 5000 cards coming out soon), more RAM, or a faster CPU, it’s not always necessary to have a computer on the cutting edge of tech.
For those who enjoy gaming, whether you use a mid-range or even a low end-device, there are still plenty of games that have come out recently as well as in the past that can reasonably run on lower end devices. While Windows 11 is still adamant about restricting what kind of hardware it can run on, many apps will likely still support Windows 10 for quite awhile even if official Microsoft support has ended. For example, Windows 7 came out all the way back in 2009 and it took until around the early 2020’s for apps like Chrome to finally start phasing out support for the OS. Tired of dealing with new Windows versions? There are also other operating systems (like Linux) you could look into for breathing new life into your older devices.
If you would like to learn more or have an older device you need help figuring out what to do with, visit me at Computers & More of Raton and I’ll be happy to help you out. Located at 800 S 2nd Street in Raton’s Business District, our hours are Thursday and Friday, 9:00 am – 2:00 pm.

BITLOCKER Bug
Posted January 25, 2024
by Bryan Stetser
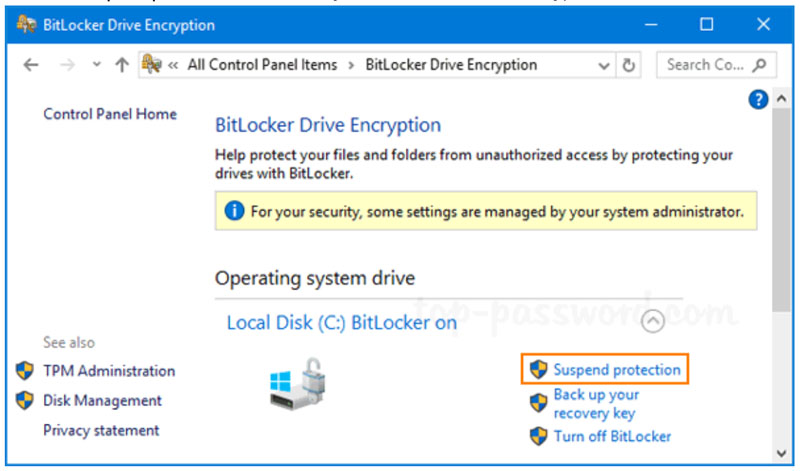
It seems that with the newest version of Windows having been out for 4 years now, there still doesn’t seem to be an end to the problems that come about.
Bitlocker Recovery has been a popular way to help encrypt your data from intrusive thieves, but that doesn’t mean it’s completely flawless. One bug that seems to have popped up with a recent update seems to prevent users from modifying settings related to Bitlocker encryption. In certain versions of Windows 11 24H2 (and older versions), when trying to modify Bitlocker settings in the control panel, you might run into a problem where Windows will toss up a message saying “For your security, some settings are managed by your administrator”. Normally this message pops up for business users who are operating on managed systems to stop them from changing things they aren’t supposed to, but there’s a chance that this bug will prevent regular users like you from changing Bitlocker settings.
So far Microsoft has confirmed that this bug is occurring on devices that are either unmanaged or have TPM (Trusted Platform Module) support with Bitlocker enabled. While it is currently unknown when this issue will be fixed, for now you should be careful with enabling Bitlocker usage, and ensure having your data backed up elsewhere in case something happens, or just hold off updating for a period of time, particularly if things seem to be working fine.
Make sure you keep on reading to hear about more tech bugs and problems, and if you have tech issues or problems, shoot me an email at bstetser@gmail.com; I’ll do my best to help you work through problems you may be having.

Gaming News: Nintendo Announces Switch 2 Release
Posted January 18, 2024
by Bryan Stetser
Hello again, even though we are only a few weeks into 2025, tech and game news is starting off strong!
For you gamers, Nintendo has finally announced the release of the Nintendo Switch 2, their follow-up to the Nintendo Switch console which came out back in 2017.
At first glance, it seems the device is a noticeable improvement with a bigger screen, a pair of refreshed Joy-Cons which connect magnetically (compared to how the older Joy-Cons would slide and snap on), as well as a teaser for a new upcoming Mario Kart title with up to 24 racers in a singular race. Not only that, but it has been confirmed that your Switch 1 games (both physical and digital) will work on the Switch 2 out of the box outside of some specific titles which we will probably find out about later on.
While leaks and rumors have been going around for the past few months or so, it doesn’t seem like Nintendo has revealed specific technical specs or how powerful the device really is, as those will likely be saved for the upcoming “Nintendo Direct: Nintendo Switch 2” on April 2, 2025. The Switch 2 is not available for pre-order yet and probably won’t be until after the Direct but Best Buy will let you register your interest and this is a great way to have updates sent directly to you.
I haven’t decided on whether I’ll be getting the Switch 2, but if I do, you can be sure I’ll be posting an article about it!
If you or a friend would like to see the trailer for yourself, click the link below and let us know if you’re planning on getting one when it comes out!
Nintendo Switch 2 – First-look trailer – YouTube

Google Chrome Browser Extensions
Posted January 11, 2025
by Bryan Stetser

One of the most popular web browsers (for better or worse) is Google Chrome. Even if you are quite familiar with using it and how it works, you may not be aware there are small software programs called “extentions” which interface with Chrome and can help customize your browsing experience.
You simply install the extensions onto your browser for extra functionality that Chrome isn’t providing by default. These extensions can be found on the Chrome Web Store (https://chromewebstore.google.com) and they are free.
Chrome extensions are designed to work with the Chrome desktop browser, and while they technically can work on the mobile app on your phone, Chrome doesn’t support extensions on Android devices.
If you like extensions and really want to use them on your phone based browsing, other Chromium-based browsers (such as Microsoft Edge and Amazon Silk) do support mobile extensions.
Extensions can be quite useful when it comes to internet browsing and I think the following are worth checking out.
Ublock Origin is an extension that automatically filters out and blocks various pop-ups and ads on whatever web page you are on, and is especially helpful if you’re on a page infested with intrusive ads. (If you are using Chrome though, the regular Ublock Origin app is currently unsupported, though it does work on Microsoft Edge or you can use Ublock Origin Lite instead).
Dark Reader is another helpful extension for those who’d prefer not to be blinded by bright lights at night as it not only inverts bright colors to make them less harsh in darker environments, but allows you to manually adjust the brightness, contrast, and more to suit your standards.
Bitwarden encrypts and secures your user data such as usernames, passwords, etc over the cloud, as well as auto generates passwords for new sites that you make accounts for. (If you don’t want to think up a new one on your own). Bitwarden is a nice alternative to Chrome’s native password manager.
While there are plenty of extensions that can be useful in many situations, it doesn’t automatically mean all of them are 100% safe. Sometimes malicious extensions can slip on through past detection and lurk around as a ticking time bomb, waiting for someone to download and use it so they can expose your personal data. Sometimes even well-trusted apps can have their faults.
LastPass (Password Manager) suffered from various data breaches and Honey (an extension that was formerly used to automatically check around for coupon codes online for good deals) is now under fire for silently swapping out affiliate links (products sponsored by online creators) for internet deals with their own to steal profit away, as well as times where it will intentionally pick coupon codes with lower discount percentages to garner more profit for the retailers.
If you are going to browse around for extensions to use for Chrome or Edge, the best piece of advice I can give you is to do your own research and double-check that what you are about to install is safe before you click on that “Get Extension” button.

Is TikTok’s Time Up?
Posted January 4, 2025
by Bryan Stetser

Happy New Year, everyone! Hopefully you all had an enjoyable time closing out 2024.
As 2025 starts rolling in, the world of tech news, more things are happening constantly, one of which relates to the social media site TikTok. If you haven’t been keeping up with what’s been happening, starting on January 19th of this year, Tiktok will be banned from operating or being accessed in the US unless it changes hands to a different, government-approved owner not associated with the Chinese market.
Starting around 2019, a growing distrust against the people behind the site, Bytedance (owner of TikTok), spread to various countries such as India as well as various regional governments in the US, the UK, and New Zealand to name a few. The fear of foreign influence isn’t anything new as there were previous bans against equipment coming from Chinese tech company Huawei. More recently, Kaspersky AV was banned from being used or sold in the US. Click here to read my article about that ban.
Regarding TikTok, even if some people believe the website should be banned to protect personal user data from being harvested by the Chinese market, others believe it’s another case of the government taking aim at freedom of expression, as well as hurting the users and content creators who frequently use it, especially since it is actually possible to make a profit from it, much like YouTube.
The highest paid TikTok influencer in 2024 commanded $259K per video thanks to his 162 million followers. Of course, not every TikTok influencer makes that kind of money; the average salary of influencers is between $15,000 and $25,000.
While January 19th is 3 weeks away, it’s still not entirely sure whether the ban will go through, be adjusted, postponed, or even actually stop people from finding alternative ways of using the app and website. It will be interesting to see what will become of those who enjoyed the fruits of their TikTok labors post ban. Remember: anything can happen when it comes to these big tech companies, and it’s not over till it’s over for TikTok in the US.
What do you think of the US banning TikTok? How will it affect you?

Arcade Style Game Controllers
Posted December 27, 2024
by Bryan Stetser

Happy Holidays everyone, hopefully everyone got what they wanted for Christmas!
Often I like playing many different video games and sometimes I like to think back to older times. One device I’ve been messing around with over the last few days is the Mayflash F700 Elite Fight Stick; a large retro controller that has a joystick on the left side with a ball top and 8 buttons on the side. It replicates the style and look of the controls you would find on an old arcade cabinet.
This device not only has compatibility for modern consoles like the PS5, but also older consoles, PC, and even mobile devices like Android and IOS via an adjustable knob on the top right. The flexibility doesn’t stop there though, as you can set the device up to run wired or wirelessly by a 2.4 USB adapter or with Bluetooth for devices that support it. You can also change the function of the joystick to serve as a left stick, d-pad, or right stick of a controller, as well as turbo functionality for the buttons to make the games that require button mashing much easier to deal with.
Even though I’ve only had this device for a few days, it’s worked surprisingly well on my Android phone and my Nintendo Switch console, working out of the box as soon as I set it with the proper input method and syncing it up. I did notice the buttons were pretty sensitive when playing with it, but I believe that was intentional since the kind of buttons that are used for this are designed to be quick and responsive for games that require fast reactions. Even though they say this stick is only for fighting games, there’s nothing stopping you from using it on other games and it works reasonably fine on other kinds of genres of games.
The only other downside of note is that it will not work on the newer Xbox consoles unless you use a controller adapter to make it work or buy a version that has Xbox Series S/X support built in (though you’d lose out on PS5 support in that case)
If you are still interested in picking up a Mayflash fight stick, check out these links:
Note: This article is not sponsored and all opinions are the author’s own.
Mayflash F700 Elite
Mayflash F700
Mayflash F700X


Stocking Stuffers!
Posted December 18, 2024
by Bryan Stetser
I’ve been adding inventory a little at a time, mostly accessories – many of which we use ourselves. If you’re looking for some last-minute stocking ideas, please check the list below, as I’ve put some on sale. We still have a few Laptops and portable Thermal Printers in stock. Once we sell out, we will no longer be carrying these items as regular inventory since there isn’t a great demand, but will be happy to help you find what you need online.
I’d like to take this opportunity to thank the community of Raton as well as my customers (new and returning) for all the support you’ve shown me in 2024. I appreciate the faith you place in me and enjoy working with each of you. Wishing you a Happy Holiday season and all the very best in the coming New Year! — Bryan

USB Wi-Fi Adapter
If you are having issues with an older PC or laptop not connecting to WiFi, try one of these adapters and get back online!
Tested on an older MS Surface tablet that lost connectivity years ago, this adapter ran flawlessly!
Price: $19.99
Christmas Sale: $14.99
Camera Cover
Keeping your camera covered is just a smart practice to safeguard against bad actors, especially if you leave your computer on all the time or use public, unsecured Wi-Fi.
Price: $1.00


USB3.0 Dual Slot Card Reader
This makes transferring data to or from your device easy. For SD/SDHC/SDXC cards. Reads up to 512G.
(cards not included)
Price: $14.99
Christmas Sale: $9.99
Cable Label Tags
Despite all the advances in technology, we still struggle with countless cords and cables!
While there’s not much you can do about that, these tags make it easy for you to see at a glance which plug goes to what.
Price: $4.75 (pack of 8 tags)


Multi-Device USB Charging Cable
In a perfect world, all rechargeable devices would have the same port. This handy cable takes the stress out of keeping track of all those cables you have to sort through to charge your devices.
Price: $12.99
Christmas Sale: $8.00
USB Multi Charging Cable
This 4-foot braided 3 in 1 rapid charging cable comes with 3 connectors: Lightning, Type C and Micro.
Price: $7.99 OUT OF STOCK


Testing Storage Devices Purchased from Temu
Posted November 23, 2024
by Bryan Stetser
Awhile back, I wrote about how to choose storage devices for data backups. That article outlined how you can make an educated guess as to the legitimacy of Flash Drives based on the capacity and price.
Because fake “high-capacity” storage devices often tend to be sold on the cheap, they are an attractive alternative to higher priced name brands. These fakes look like regular storage devices, and will appear to be high capacity when your computer reads the available space, but they are simply low capacity devices programmed to look like they hold more storage then they actually do. This can be quite troublesome as the last thing anyone wants is to find out the 1tb USB stick they just bought overwrote and corrupted itself and turned out to a 32gb USB stick in disguise. While they look legitimate to you and your computer, the sad truth is you have no way of knowing until it’s too late.
When shopping online, if the price seems too good to be true, it is. Always check the product reviews before you buy, and just stay away from a device that is significantly cheaper in price than name brands and don’t buy storage devices from places like Temu and AliExpress.
While some will say you CAN find cheap, high-capacity devices on the above sites, I decided to buy a handful of cards and a USB stick to test and find out what the odds were of getting a legitimate device while saving myself a lot of cash.
Two free applications are available for testing storage devices. They are H2TestW and f3probe. These tools stress test the device by checking how fast or slow it is as well as writing across the entire device to check if the reported capacity is accurate and determines if the card has faulty sectors that can’t be written to. If you choose to test devices, be aware that the testing process will wipe out any data already on the device, so any testing should be on a device before you write anything to it.
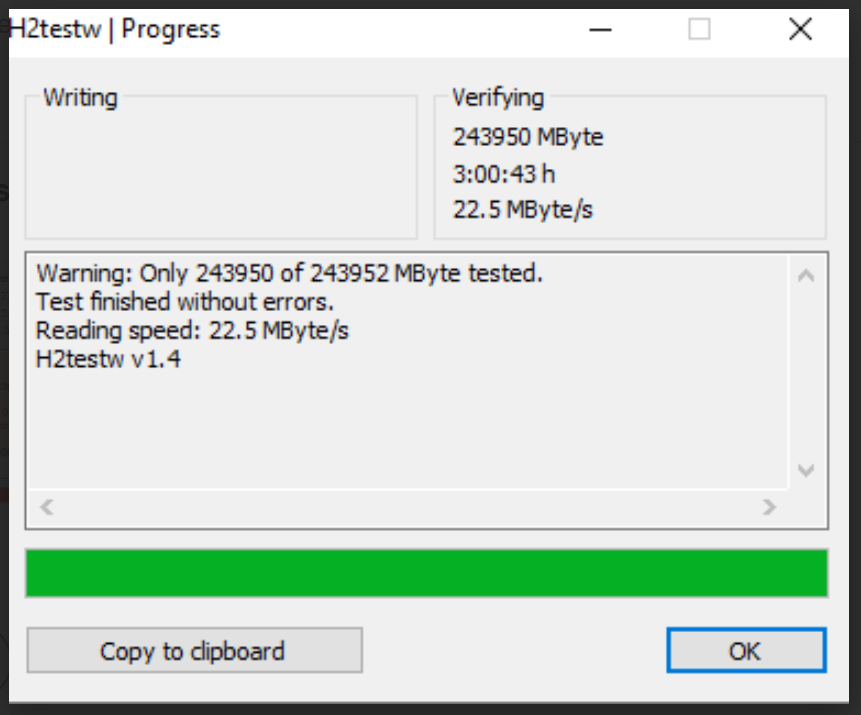
I conducted my testing using H2TestW on a Dell notebook running Windows 10. The test using this program is in two phases: the first phase writes data to the card while the second phase verifies.
My first test was on a SanDisk 256gb microsd card. This took a total of 3 hours to complete both phases and verified the card to be a legitimate card. While this card appears to be just shy of 244gb, the remaining space not reported on is utilized for formatting of the card. All storage devices use some available space for formatting. Here is a screenshot of the results:
Next I moved on to begin testing the Temu devices, starting with a 128gb generic looking microsd card. The testing time for this card (which was half the size of the SanDisk), took over 16 hours to test and appeared to actually be a 16gb card.
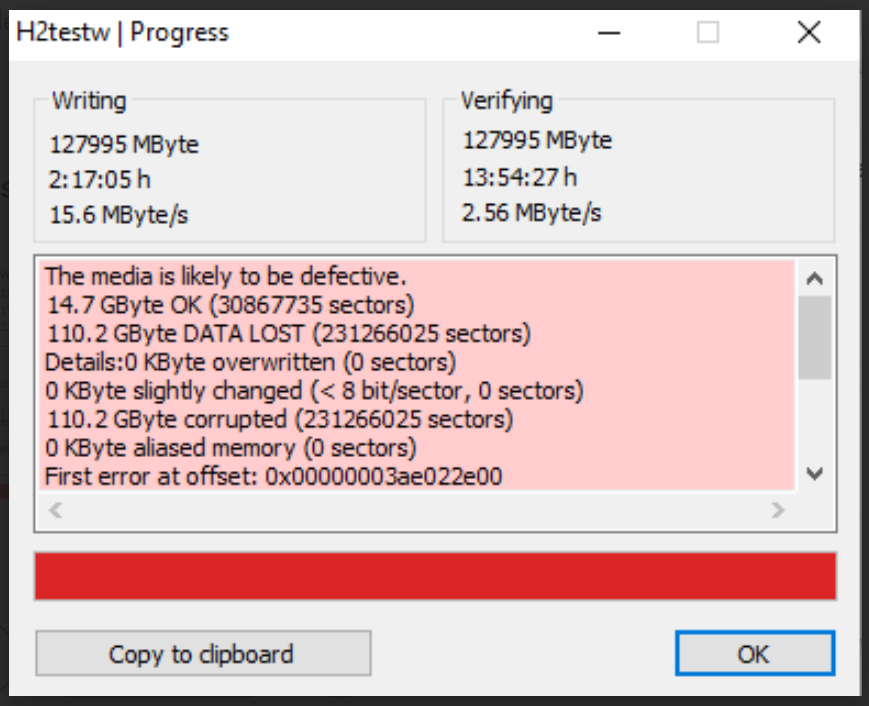
Because the estimated length of testing time increased significantly with each “larger” card, I ran the remaining tests long enough to reveal the actual capacities as well as issue errors in the writing process, indicating these card sizes were not legitimate either. I tested a 256gb and a 512gb and both appeared to actually be 32gb cards.
My last test was on a 2tb USB flash drive which was very nicely packaged and had a graphic of the Statue of Liberty on it’s case. This device took about two hours to write before it issued an error, and estimated 100 more hours to verify. It appeared to have a capacity of 128gb.
The following is what I paid for each microsd card, as well as the cost for a comparable SanDisk device:
Fake: 128gb – $4.09 SanDisk: List price $18.99 / Amazon price: $11.99
Fake: 256gb – $5.39 SanDisk: List price $25.99 / Amazon price: $18.99
Fake: 512gb – $6.92 SanDisk: List price $37.99 / Amazon price: $32.00
As for the 2tb USB Flash Drive, the cost was $5.09. Since legitimate 2tb USB flash drives do not exist for regular consumers, I don’t have a price to compare.
My total cost for the above four items was $22.74. Temu actually sent me TWO of the flash drives, then sent an apology notice for non-delivery and refunded me $11.92.
While this was a small sampling of device, there was not a legitimate drive in the group. I am confident in saying there ZERO chance of getting a legitimate storage device anywhere at these greatly reduced prices.

Portable Software for PCs
Posted October 26, 2024
by Bryan Stetser

We all have that one app we use everyday, and if you’ve ever found yourself without your trusty laptop and borrowing a computer that doesn’t have your favorite app, then portable software may be for you.
Portable apps are designed to work from one singular place; they don’t require installation and everything related to the app is all in one place. One of the most popular uses of these types of software is to load them onto and run them from USB sticks (Flash Drives). All your user settings and preferences as well as files you create are saved to the stick, eliminating the worry about files being in multiple folders and making it much easier to move your productivity between devices.
A traditional software application requires the use of an executable (.exe) installer to setup the necessary files on your device across certain folders along with extra software and changes to your system files it might need in order for the software to run. This can work fine if you only plan on using the software on just one device, but if you don’t, then it can be a pain to re-setup your workflow with said app on a new device. Portable apps are standalone and not dependent on a specific setup in order to run.
Portable software should also run without any special permissions from site administrators, although I did run into an instance where Bitlocker on a corporate laptop would not allow running anything from a stick. However, for your own personal use across devices that don’t have any extraordinary security lockdowns, you can enjoy your favorite apps just about anywhere, making them the ultimate in convenience.
There are plenty of portable versions available; web browsers like Google Chrome or Mozilla Firefox are good options for browsing the web, and VLC Player or Audacity for easy video/music access on the go. Even if applications like modern Photoshop or Microsoft Office aren’t specifically designed to be portable, you can find alternatives that can serve as reasonable substitutes, such as Krita or Libreoffice.
Portable software doesn’t stop here! There are hundreds of apps available to help you turn your USB stick into a nicely customized mini computer. These apps may also be stored and run from a local drive as well as the Cloud.
If you are interested in setting up some portable apps for your own use, stop by Computers & More at 800 S Second Street and let’s see what we can come up with. We are open Thursdays and Fridays 9am – 2pm. Please be aware we recently moved to a different section of the building and are using the east entrance now.

Is My Computer Safe During a Geomagnetic Storm?
Posted October 16, 2024
by Bryan Stetser

On Friday, October 11, 2024, thanks to perfectly clear skies, Raton was treated to a rare view of the Aurora Borealis, also known as the Northern Lights. This is the second time in 2024 that we were able to view them, although with overcast skies, we were unable to see them back in May.
I never thought I’d see them unless I went to someplace like Alaska or Norway and I was surprised when I looked for it to see just a faint pinkish glow, barely visible and nothing like the usual greenish lights and streaks I’ve seen in photos. Honestly, I was disappointed. I took a photo anyway and couldn’t believe what I had captured: the sky lit up in a bright magenta color. I’m including a graphic below that explains why the color I saw was reddish-pink and not green.
If you’d like to learn more about the Northern Lights, please visit this Capture The Atlas page which explains the Northern Lights better than I can.
That being said, you may be wondering what you should do to protect your computer from the magnetic storms responsible for creating the Northern Lights. In short, using your computer during a magnetic storm won’t directly affect or harm it. The real issue would be if the magnetic currents from a massive storm infiltrated the power grid. In this case, your surge protector wouldn’t be useful, as the currents that could adversely affect and overwhelm the grid are big, sustained surges and sags. Surge protectors are only designed to manage and provide protection against brief glitches and spikes.
Some believe wrapping electronics in foil or using a Faraday Cage is a good defense. While these two methods do block geomagnetic fields, I personally wouldn’t go so far as to resort to these methods.
In summary, the chances of your computer being directly damaged relative to a magnetic storm are pretty slim. Unplugging your computer’s power supply during a magnetic storm would prevent it from becoming collateral damage in the case of a compromised grid but bear in mind that magnetic storms can last for hours. While a laptop or tablet can run off a battery, the same isn’t true for a desktop. However, you could set up a battery backup for that type of system as well and keep your system off the grid till the storm passes.


Microsoft Hello for Windows 10/11
Posted October 12, 2024
by Bryan Stetser

If you’ve been looking for an easier way to login to your computer without needing to use a password and happen to be using Windows 10 or 11, you might find Windows Hello to be a helpful alternative.
Windows Hello allows you to login to your device in various different ways, such as using your fingerprints, facial recognition, or even a personal identification number or PIN for short. These methods come in handy if you need a quick way to login to your device, although for the first two, you will need a device that read your fingerprint scans or a Windows Hello compatible IR webcam (built-in or external) for facial recognition. (This helps stop hackers from being able to login by using a picture of your face).
These methods are also completely separate from your Microsoft password, so you won’t need to worry about someone using it to try and login to your Microsoft account. Even for the fingerprint method, you only have to worry if someone manages to steal a sample of your prints, which is unlikely to happen unless you are a very important person.
If you would like to try and set these methods up yourself, type “settings” (without quotes) in the search bar below, go to SETTINGS/Sign-in Options, and from there you should be able to choose which method you want to use. Personally I use the option to login via a specific PIN number, though feel free to choose which works best for you.
If you would like to set it up on your device and need help, visit Computers & More of Raton! We are located at 800 S 2nd Street, our hours are Thursday and Friday, 9:00am – 2:00pm. We look forward to assisting you and are excited to serve you in our new space. Please use the east entrance to access us in the front of the building.

WE ARE MOVING!!!
Posted October 4, 2024
by Bryan Stetser

I’m pleased to announce Computers & More of Raton is moving! Not very far, just to the front of the building I’m currently in. Since we’ve made an epic mess in both the old and new spaces, I’m busy getting things back in order and there won’t be a column this week.
In addition to the small stock of laptops and mobile printers, there have been some new and interesting things added to the inventory.
I look forward to welcoming you to a brighter and easier to access shop! Starting Thursday, October 10, please use the door on the east end of the building when you visit. Hours are still Thursday and Friday, 9:00 am to 2:00 pm.
It has been a pleasure to serve your computer needs and I am so grateful to a community that has placed its trust in me. Thank you, Raton!

Windows 11 Recall Feature
Posted September 28, 2024
by Bryan Stetser

As of recently, Microsoft has been making some “interesting” changes to their newer versions of Windows. One controversial feature that has been recently introduced to Windows 11 is called “Windows Recall”.
Windows Recall allows for your device to take screenshots on your device (which are stored locally on your drive) to help record and track your activity. If you don’t know where or what specific file you need, Recall uses a mix of AI (Artificial Intelligence) and Optical Character Recognition to find what you need. While it can have benefits for remembering specific files or moments, it is another case of Microsoft forcing another feature that not everyone is a fan of, given concerns about AI algorithms gathering data and Microsoft’s infamous history of harvesting user information. It may also allow hackers to access your date. This is a major reason why I don’t use it personally.
While it has been temporarily removed from Windows 11 due to privacy concerns and won’t be back until around October, you can also turn it off by going to SETTINGS/PRIVACY & SECURITY/RECALL & SNAPSHOTS, then turning it off from there.
If you prefer to remove it entirely, you can also use the search box to search for “Turn Windows Features On or Off” and uncheck Recall from there.
If by any chance you need help getting rid of these new features or you are interested in learning more about other operating systems, feel free to visit me at Computers and More of Raton on Thursdays or Fridays from 9:00am – 2:00pm. The shop is located at 800 S 2nd Street.

Kaspersky Migrates Users After US Ban
Posted September 21, 2024
by Bryan Stetser
If you haven’t been keeping up with Kaspersky AV ban lately, you might not have noticed that they’ve been going through some rough spots. Around June 20th 2024, they had been forced out of the US market due to accusations of exposing user data to malicious Russian actors.
For the people who may have still been using their anti virus, Kaspersky recently decided to migrate these users to a different anti virus service by the name of UltraAV. This anti virus happens to be owned by a company called the Pango Group which resides in Boston and handles general online safety activity.
While I have not used any of their services to make a proper judgment on them, now might be a good time to consider if you still want to use Kaspersky’s services or move to a different provider.
I personally use a combination of Windows Defender to handle most threats and Malwarebytes for the threats that slip through; both of which are free. If you use and are interested in switching away from Kaspersky, come to Computers and More of Raton at 800 S 2nd Street and let us help you figure out what options are available to you. Our hours are Thursday and Friday, 9:00am to 2:00pm.

Windows File Explorer Preview Pane
Posted September 14, 2024
by Bryan Stetser
You might have wondered if there is an easy way to view your Windows File Explorer without opening them outright in their associated applications, like images for example.
At the top of the File Manager, there is a tab labeled VIEW which allows you to customize how your file lists appear. There are several options, from simple lists to icon views which display miniature images of your files. The icons are a handy way to help identify what a particular file is, but they are also that – miniatures, and may not provide enough detail to determine if it’s the file you are looking for.
There is another option that is an even easier way to view your files without opening them one by one and it works with all sorts of files. It’s called the Preview Pane.
If you don’t already have it enabled, open up the File Explorer, click on the VIEW tab, then click on Preview Pane. This option will display a much larger preview of the file located to the right of the files. With it, you can quickly preview your documents, pictures, videos, and more all without having to open them up. Whether you use Windows 10 or 11, try it out and see how much easier it is to quickly preview your files.

Should You Defrag Your Drive?
Posted August 30, 2024
by Bryan Stetser
While most computers have long since moved onto using Solid State Drives for storage, there are still many that use regular Hard Disk Drives. Over time, these hard drives will start to slow down and take longer to access files, especially if you use a hard drive as your main drive for Windows.
Part of the reason for laggy file retrieval is due to how computers store files. As a drive fills up, there may not be enough space to store an entire file in one place, so your computer will break it into pieces (fragments) and store these pieces in different areas of the drive. The next time you open the file, the computer gathers up the pieces and displays it in its entirety.
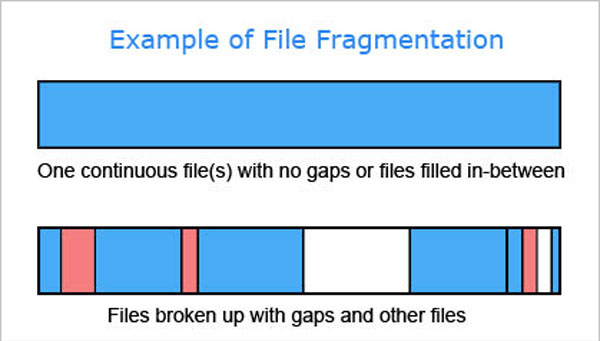
For Hard Disk Drives only, a good way to speed up your drive if it’s been running slower than usual is to consider defragmenting it.
Defragmentation (also known as defragging) involves rearranging the data found on a drive into contiguous segments, which greatly reduces the time needed to access the file. Windows tends to handle defragmentation in the background automatically, but if you want to manually do it yourself, type “Defragement and Optimize Drives” (without quotes) into the search bar at the bottom left of your screen. From there, you can modify when you want Windows to automatically defrag your drive or even do a manual defrag on the spot.
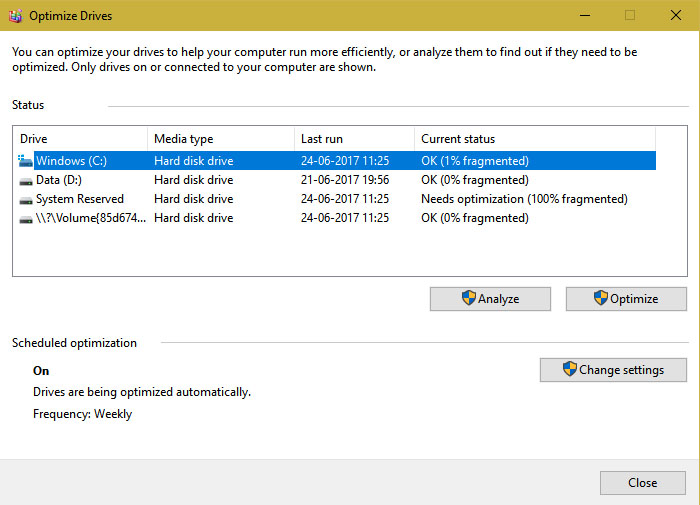
If you’re doing a manual defrag, you’ll see something like this and will be able to watch the progress as your computer gathers your files back up.
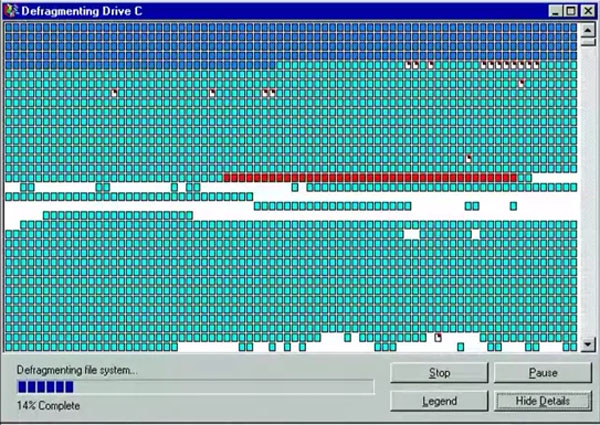
Keep in mind: defragging a solid state drive is not recommended as it will either do nothing at best or significantly reduce write cycles that your Solid State Drive uses at worst, thus reducing its lifespan. Defragging a SSD won’t break it, so if you have already defragged it, your drive will be OK. Just don’t do it again!
If you would like some assistance with defragging your hard drive or would like to look into upgrading your hard drive to a solid state drive, stop by Computers & More of Raton and let’s figure out what might work best for you. We are located at 800 S 2nd Street and open Thursday and Friday 9:00 AM – 2:00 PM.

Disposing of E-Waste
Posted August 23, 2024
by Bryan Stetser

Computers, laptops, phones and other electronics serve us well over time, but eventually things get to a point where one has to make a decision about equipment disposal (e-waste). Today’s article covers properly disposing of your devices.
While it might be tempting to just chuck your device into the regular household trash and let waste disposal handle it, this is not the most responsible practice and can be dangerous. Not only does this practice further pollute the environment, Lithium batteries can be dangerously explosive if damaged. You also put yourself at risk with the theft of personal data left on your device.
If you are considering getting rid of your device, do consider backing up whatever data you might have on there, then format to wipe it clean. This helps ensure malicious actors who may grab your laptop from the trash can’t easily get your data. If you are still worried about your data being stolen, you could remove the drive and either manually destroy it or take it to a professional to dispose of it.
Once you’ve removed your personal data, you have several options for what you can do with your device.
- You may be able to trade your device back to the place you bought it from and potentially save money on future purchases.
- You could find someone willing to buy it through places like Facebook Marketplace or eBay and make some money in the process.
- You could donate your device to a charitable organization so others who are less fortunate have access to technology they otherwise couldn’t afford.
- If you wish to permanently dispose of the device, there are many e-waste disposal services which accept equipment. Usually there is a fee associated with e-cycling.
Luckily for those of us in Raton, the Hereford Collection Center Solid Waste and Recycling Facility accepts e-waste at no charge! Located at 410 Hereford Avenue, there you’ll be able to safely and easily dispose of your electronics without causing potential risk to the environment.
If you’d like to learn more or need help deciding what you want to do with your data, come on down to Computers & More of Raton and we can discuss your needs further. We are located at 800 S 2nd Street and our hours are Thursday and Friday, 9:00am – 2:00pm.

Ethernet vs Wi-Fi
Posted August 16, 2024
by Bryan Stetser
The internet is an essential part of modern life all across the globe and as a digital lifestyle is the rule rather than the exception, we continuously strive for faster and more stable internet access. While many are fine with using Wi-Fi to use the net, Ethernet is by far a more secure, consistent and faster method.
Wi-Fi is of course more convenient; simply put, radio waves deliver the internet to your portable devices giving you the freedom to use your device just about anywhere. This freedom can come at a price, with range issues as well as being subject to electrical interference that can cause connectivity speeds to slow or drop altogether.
Ethernet, however requires a physical cable connecting your equipment to the modem. This direct connection gives you faster speeds and stable connections to just about anywhere in your house (assuming you have an average sized home). However, Ethernet can be constraining and create clutter with extra cables to deal with, but for someone like a hardcore gamer, this is usually a fair tradeoff.
If you decide to go with Ethernet, buying cables can be confusing, so I’m going to break down what you can expect to choose from and how to decide what to buy.
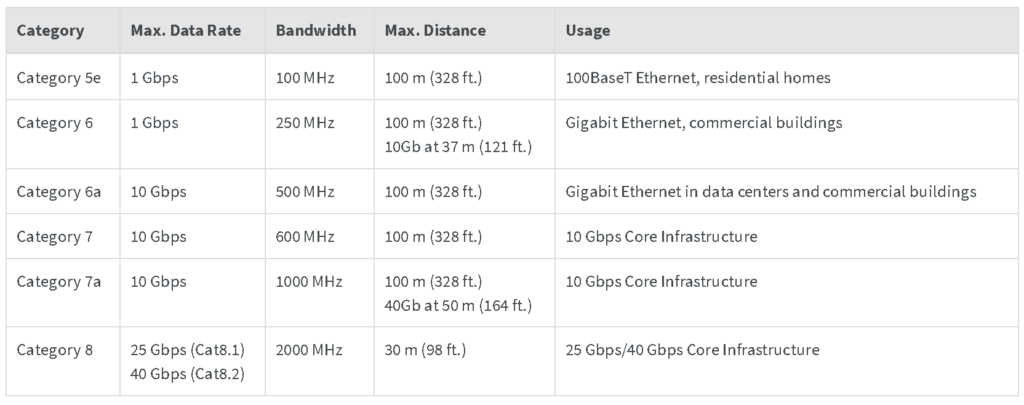
Ethernet cables are typically called “Cat” followed by a number. Cat stands for Category and the number refers to the maximum data transfer rate the cable can manage. I’ve included a chart below to show you see the differences in cables
Category 1-5 Ethernet cables were in use from the late 80s/90s. For today’s technology, they are too slow for daily use or not really used anymore at all, so I won’t go into detail about them.
Cat5e cables (the e standing for enhanced) are similar physically to regular cat 5 cables, but tend to suffer less from crosstalk issues (when one set of cables causes interference with other nearby cables), which makes them a reasonable choice for homes and offices for their low price costs and reasonable support, though speedwise they aren’t super fast. The average cost of a 10 ft Cat5e cable is between $2.50-$5.00 depending on where you buy it.
Cat6 and 6a (augmented) cables are designed to be more shielded physically as well as able to support higher bandwidth They are more pricey and can be found for around $5.00-$10.00 for a 10 foot cable.
Cat7 and 7a cables are a step up over the others, but they don’t tend to see much use these days due to the proprietary connector making it harder to set it up with previous ethernet standards.
Cat8 cables are the newest and by far the fastest cables around for ethernet usage, potentially reaching up to 2,000 MHz frequency and supporting speeds of 40Gbps up to 30 meters, as well as being covered and shielded up by default, meaning the connection stays stable and consistent.
If you are looking for ethernet cables and are on a budget, I recommend you stick to Cat 5e or Cat6 ethernet cables, but if you want to future proof your home and have the money, get yourself some Cat8 cables for the speed and efficiency. If you are interested in picking up some ethernet cables, I have a few shorter Cat6’s in stock, and you are welcome to visit Computers & More of Raton to learn more.

Kaspersky AV Banned in United States
Posted August 9, 2024
by Bryan Stetser
As we struggle to keep our devices safe from malicious threats, AntiVirus software must remain constantly in use. News about one of these AVs has been making the rounds recently: Kaspersky AV.
Released all the way back in 1997, it is known as a Russian-developed AntiVirus that has serviced over 400 million users and around 220 companies worldwide. It has come under fire recently for potentially exposing user data to certain Russian actors*, and this was a big reason for the US Commerce Department banning usage of this software back on June 21, 2024. Kaspersky began closing down operations in the US a month later starting on July 20, 2024.
If you happen to be using Kaspersky AV still, it is time to look into some alternative options for AntiVirus software. Windows Defender is still very capable as an AntiVirus tool that’s been directly built into Windows since Vista and has been improving with each new version, usually being enough to keep your system safe. Another good option to keep along with Windows Defender is Malwarebytes, which has both a free and paid version. Even if you don’t pay for the full version, it still does an excellent job of scanning through and detecting malicious files and getting the job done without constantly spamming you with popups to buy it.
If you have Kaspersky installed on your computer and would like to uninstall it, open up the Start Menu, go to SETTINGS and search up apps and features (or do it through the search bar), then scroll down till you see Kaspersky. Click on it if you are on Windows 10 (or the 3 dots on the side if using 11), then click on the uninstall button and proceed through with the steps to remove it from your system.
If you need help uninstalling Kaspersky or would like to further discuss AntiVirus software, stop by Computers & More of Raton so we can help set your computer up for safety and security.
We are located at 800 S 2nd Street (across from BTU) and are open 9:00am – 2:00pm, Thursdays and Fridays.
* Actors: a Threat Actor is someone with malicious intent. They may or may not possess the same level of technical skill as a hacker, but their primary goal is to cause harm or disruption. (from Google)

BITLOCKER for Data Encryption
Posted August 2, 2024
by Bryan Stetser
From Microsoft: BitLocker is a Windows security feature that provides encryption for entire volumes, addressing the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned devices.
——————–
As technology continues to advance and hackers find new ways to hack into places they don’t belong, we look for more ways to keep our data safe from oncoming threats. We password our computers and WiFi, run Anti-Virus and Malware protection and hopefully all practice vigilance and care when we are visiting websites or being wary of suspcious email links. These are all good practices and safeguards.
In an earlier article, I discussed Remote Access Software which can allow you to grant another person online access to your computer and how risky that can be if the wrong person gets in. If you didn’t read that article, you might not know it, but if someone were to remotely access the drives in your computer, they could easily steal your personal data, no matter how good your passwords are. There are still a lot of people falling victim to smooth-talking, convincing scammers who prey on the fact that most people are inherently trusting. This alone is a good reason to look into drive encryption as an added layer of protection, especially for vulnerable users.
One method is the subject of today’s article: Bitlocker.
Bitlocker’s been around since Windows Vista and Windows 7. I think most people might assume it’s corporate sofware. Keeping with more recent operating systems, for people who have a copy of Windows 10 or 11 Pro, Bitlocker may be something you’d wish to consider.
Bitlocker is an encryption system that allows you to further secure the data on your drives. Encryption turns data into code, making it unreadable to anyone without the proper decryption key. It’s a robust system of protection and worth having.
While it’s protection can be a blessing, it can also be a curse if you don’t keep track of your recovery method, (recovery codes are usually tied to your Microsoft account, but they can also be stored on a flash drive), as it will not let anyone access the affected drive without proper authentication. Meaning it can be easy to lock yourself out of your files if you don’t keep track of things.
At that point, if you don’t have a way of getting the recovery code or PIN, your won’t be able to access your data. We all forget our passwords or PINs, and obtaining new ones is generally not overly complicated, but when it comes to Bitlocker, it’s all or nothing and a price you could potentially pay for ensuring the safety of your drive using encryption.
Bitlocker can also be used to encrypt external drives (including USBs) and is only available for the Windows platform.
Most times on devices with Windows 10/11 Pro, Bitlocker is enabled by default, though if it isn’t, you can turn it on by searching for “Manage Bitlocker” in the Windows search bar. Upon turning it on, you’ll need to setup a flash drive or password, save your recovery code somewhere, then choose whether you want to only encrypt the disk space that’s currently being used (For newer, faster pcs) or to encrypt the entire drive (for older pcs).
There are other forms of encryption available if you don’t have Windows Pro edition, but Bitlocker is well-known and more widely used. No matter what encryption method you choose to use, as long as you keep your recovery method safe, this is an excellent safeguard against malicious hackers trying to steal your personal data.
** I can verify the effectiveness of Bitlocker against unauthorized access having once been requested to try to bypass it for a customer. I spent hours and tried every trick in the book, without success.

Crowdstrike Outage
Posted July 28, 2024
by Bryan Stetser
If you’ve been keeping an ear out for recent tech news, you may have heard of the recent Crowdstrike outage that happened a week ago. This incident caused many windows devices owned by various companies to become bricked without warning, thanks to a faulty update. All of this would occur due to a null point exception (what happens when a program tries to read outside of memory that it’s not supposed to), which would cause devices affected by the issue to crash with the ever infamous blue screen of death and begin boot looping (a failure to complete the boot process resulting in the device cycling unsuccessfully through the process).
There was at least one way to fix it if you were unfortunate enough to update and run into this problem, though it would require manually booting into safe mode, going into your drivers folder in your system32 directory and manually deleting the affected “C-00000291.sys” file causing the problem. While it might have been reasonable to fix for some devices, others weren’t as lucky, and if your device was encrypted with Bitlocker protection, you would need a recovery key which would be hard to obtain if it was on a server also suffering from the Crowdstrike crash.
While the incident only seemed to affect Windows luckily (or unluckily enough depending on what system you use), all systems can still have moments of running into problems like these, especially Linux which had a similar but lesser known situation regarding Crowdstrike just 3 months prior.
If there is a lesson to be learned from this, it’s to always remember to wait a bit before jumping on the latest updates for your system until you know it’s safe and make sure you have a recovery plan in mind in case something goes wrong. Perhaps sometime in the future, Microsoft will start locking down devices from being able to mess around with the device kernel to avoid a repeat of this situation, though only time will tell if this will occur again.

My Amazon Prime Day Picks
Posted July 16, 2024
By Bryan Stetser

UPDATED 7/20/24:
Prime Day has come and gone. I’ve decided to leave this post up for my regular Sunday article as these items are still worth sharing. I’ve updated the items with prices current as of today. Amazon does often adjust pricing up and down throughout the year and a lot of their products are discounted even on non Prime days.
Amazon has only one Prime Day event per year, but if you are interested in possible future deals on items below, they have a few more events which may again offer deeper discounts on the items below which may match Prime Day.
Amazon Early Access Sale: another two-day event usually held in October (for holiday shopping, Prime Members have the opportunity to shop deals ahead of non Prime members). Amazon has not yet announced a date for 2024’s Early Access Sale.
Black Friday and Cyber Monday: These days offer more holiday shopping deals. Black Friday falls on the day after Thanksgiving and Cyber Monday falls on the Monday after Thanksgiving.
Happy Prime Day everyone! If you are looking for some good deals on Amazon during their two-day Prime Event and happen to have a Prime membership (or know someone who does), here are a few of my recommendations for products I found while looking around. Keep in mind that you will need an active Amazon Prime membership to take advantage of these deals. You do not need Prime to use the Amazon brand devices though, like the Amazon Echo for example but you will need to create an account if you don’t aleady have one. The Blink Security Cameras and Amazon Smart Thermostat can both be controlled via voice commands if utilizing the Alexa app or through Echo Dot and Echo Show.
This is a non-sponsored article. Prime Days run July 16-17, 2024. Thank you for reading.
Sandisk 512 GB A2 SD Card $39.20 (Prime Price was $31.99 16% off)
https://www.amazon.com/SanDisk-256GB-microSDXC-Memory-Adapter/dp/B0B7NVXLLM?ref_=ast_sto_dp&th=1&psc=1
Amazon Echo Dot $49.99 (Prime Price was $24.99 50% off)
https://www.amazon.com/All-New-release-Smart-speaker-Charcoal/dp/B09B8V1LZ3?source=ps-sl-shoppingads-lpcontext&ref_=fplfs&psc=1&smid=ATVPDKIKX0DER
Amazon Echo Show 8 $149.99 (Prime Price was $84.99 43% off)
https://www.amazon.com/All-New-Echo-Show-8/dp/B0BLS3Y632/ref=asc_df_B0BLS3Y632/?tag=hyprod-20&linkCode=df0&hvadid=692875362841&hvpos=&hvnetw=g&hvrand=3686256872693020514&hvpone=&hvptwo=&hvqmt=&hvdev=m&hvdvcmdl=&hvlocint=&hvlocphy=1014485&hvtargid=pla-2281435176378&psc=1&mcid=2da1903c149533349f407e553085087a&hvocijid=3686256872693020514-B0BLS3Y632-&hvexpln=73&gad_source=1
Ring Doorbell with indoor chime: $124.99 (Prime Price was $69.99 44% off)
https://www.amazon.com/Ring-Video-Doorbell-Venetian-Bronze-with-Chime/dp/B09PWG8KNC?ref=dlx_prime_dg_dcl_B09PWG8KNC_dt_sl7_15
Blink Outdoor Security Cameras (can also be used indoors): $399.99 (Prime Price was $159.99 60% off)
https://www.amazon.com/Blink-Outdoor-4th-Gen-5-Camera/dp/B0B1N4LM4J?ref=dlx_prime_dg_dcl_B0B1N4LM4J_dt_sl7_15
Amazon Smart Thermostat: $79.99 (Prime Price was $51.99 35% off)
https://www.amazon.com/Amazon-Smart-Thermostat/dp/B08J4C8871?ref=dlx_prime_dg_dcl_B08J4C8871_dt_sl7_15
Crucial 1TB SSD Laptop Drive: %67.76 (Prime Price was $59.99 37% off)
https://www.amazon.com/Crucial-BX500-NAND-2-5-Inch-Internal/dp/B07YD579WM?ref=dlx_prime_dg_dcl_B07YD579WM_dt_sl7_15&th=1
Anker 6ft USB / USB-C Cables (2 pack): $9.99 (Prime Price was $7.99 38% off)
https://www.amazon.com/Anker-2-Pack-Premium-Charging-Samsung/dp/B07DC5PPFV?ref=dlx_prime_dg_dcl_B07DC5PPFV_dt_sl7_d1&th
TESSAN 5ft Power Surge Protector: $19.99 (Prime Price was $16.99 23% off)
https://www.amazon.com/TESSAN-Extension-Charger-Charging-Essentials/dp/B0B5CNGKRH?ref=dlx_prime_dg_dcl_B0B5CNGKRH_dt_sl7_d1
Logitech Wireless Mouse: $27.99 20% off (List price is $34.99, currently still priced as Prime Day Pricing)
https://www.amazon.com/Logitech-M705-Wireless-Marathon-Mouse/dp/B087Z733CM?ref=dlx_prime_dg_dcl_B087Z733CM_dt_sl7_d1&th=1
PNY 512gb ISB 3.0 Flash Drive: $34.99 (Prime Price was $29.74 22% off)
https://www.amazon.com/PNY-Turbo-Attach%C3%A9-Flash-5-Pack/dp/B0BF5VHLBZ?ref=dlx_prime_dg_dcl_B09RG1TNM7_dt_sl7_d1&th=1
SanDisk 256GB iXpand Flash Drive Luxe: 2-in-1 USB for iPhone, iPad, and Computer: $59.99 (Prime Price was $50.39 44% off)
https://www.amazon.com/SanDisk-iXpand-iPhone-Type-C-Devices/dp/B08JD2LXXG?ref=dlx_prime_dg_dcl_B08JD2LXXG_dt_sl7_d1&th=1

Passkeys
by Bryan Stetser

As we have become almost completely reliant on the internet, security continues to be ever important. For many, passwords are the most important factor in keeping your personal information from falling into the hands of cybercriminals.
While there are methods of varying effectiveness to protect your online accounts, such as having strong passwords and using 2-factor authentication, another method of safeguarding your account is also available: passkeys.
Passkeys rely on a combination of a public key (stored on the website) and a private key (stored on your device) together to allow access to sites. Usually these keys are also associated with various functions of the device being used, like using fingerprint recognition, facial recognition, or even entering in your devices pin number and eliminate the need for traditional passwording. They can also be synced across different devices as well, so you don’t have to worry as long as you don’t lose access to your device before syncing over.
Keep in mind that while certain sites do support passkeys like Google and PayPal, not every site supports them yet. Considered more securel, they aren’t foolproof, as malicious hackers can still work around this with methods such as using malware to steal your browsers’ “cookies” (personal information that sites use to remember you).
Check to see if the sites you are using support passkeys and considering giving them a try.

We Almost Had a Winner…
by Bryan Stetser
Rich Kuhns came the closest to winning the text abbreviations contest, missing just one! This was a tough contest, wasn’t it? Many of us use the abbreviations and/or know what they refer to, though! Here are the answers and thanks for participating!
If anyone wants a Phone Pocket which were the prizes, come see me at 800 S 2nd Street on Thursdays and Fridays between 9:00 AM and 2:00 PM!
1: OTP
2: PIN
3: QR Code
4: SMS
5: MMS
6: WIFI
7: GIF
8: GPS
9: KYC
10: PDF
11: PNG
12: JPEG
13: URL
14: WWW
15: PAN
One Time Password
Personal Identification Number
Quick Response Code
Short Message Service
Multimedia Messaging Service
Wireless Fidelity
Graphics Interchange Format
Global Positioning System
Know Your Customers
Portable Document Format
Portable Network Graphics
Joint Photographics Experts Group
Uniform Resource Locator
World Wide Web
Permanent Account Number

Contest Time – CLOSED
by Bryan Stetser

This week in place of our regularly scheduled article, we will be doing something special this time.
We’ll be running a little competition that’s open only to those who are currently residents of Raton, New Mexico. Down below is a list of popular text abbreviations and it will be your goal to figure out what the full word is for each abbreviation without looking them up.
The first 5 people to send me the correct answers for all of them on Facebook Messenger or at bstetser@gmail.com will receive a phone pocket prize that you can stick on the back of your phone to carry essentials. All winners will be announced here next Sunday as well as on our Facebook page. There are 15 abbreviations in total; best of luck!
1: OTP
2: PIN
3: QR Code
4: SMS
5: MMS
6: WIFI
7: GIF
8: GPS
9: KYC
10: PDF
11: PNG
12: JPEG
13: URL
14: WWW
15: PAN

Artificial Intelligence
by Bryan Stetser
As AI continues to grow and advance over time, it is important to learn about what it is and its influence over the internet today.
AI or Artificial Intelligence is a form of technology that allows for machines such as computers to emulate human-like behaviors to perform specific tasks. These behaviors can vary wildly, from simulating behavior for NPCs (non-player characters) in video games, to generating visual pictures or recreating peoples voices. The main subject we’ll be talking about today is Chatbots, which is probably familiar to most.
AI Chatbots are mechanical information banks, which pull from a source of information and emulate talking to a real person by employing machine learning. While they have existed for many years (like Eliza, an early chatbot made around 1966), they have become more noticeable on websites like Amazon and Walmart for examptle using AI Chatbots for their customer support, as well as general AI assistants like Amazon’s Alexa or Apple’s Siri.
There has been a sudden surge in popularity over the last few years with the rise of services like ChatGPT and Microsoft Co-Pilot; services which allow you to ask them to do specific things. This could include things like designing web applications or solving complex math problems to name a few. In certain cases, one might find it simpler to ask a Chatbot a question about a difficult subject or a company may even use Chatbots in place of humans for customer support to simplify interactions between the customer and allowing for instant responses.
However, these AI Chatbots aren’t always perfect, sometimes getting information wrong and needing to be corrected, as well as requiring safety mechanisms in place to keep them on topic. Without it, you can run into situations where the AI might do or say something bad, like recommend a discount for a service it can’t actually grant or suggest a solution to a problem that will cause a great risk of harm.
While I am not fully against AI as a whole, I do err on the side of caution as it continues to become more mainstream. Many companies like Google are relying more on it and they don’t always prepare for the worst case scenario.
Google recently pulled down their AI Chatbot “Gemini” after it went on a streak of suggesting questionably wrong, if not dangerous statements while searching on Google. Microsoft also used to have a Chatbot named TayAI which they ended up having to take down years ago after various Internet users influenced and corrupted it, rather then having it read from legitimate sources.
Situations like these can quickly turn these Chatbots from reliable helpers that can provide legitimate answers to your questions into becoming dangerous and completely unreliable.
While it might take a long while and plenty of work before it will get to the point where AI replaces regular human interaction, its highly unlikely AI is going away. AI isn’t bad on its own, but we should be looking into having things like Chatbots continue to work together with humans and having proper safety rails in place, rather than to be fully self automated as there are still too many variables that can cause negative consequences.
At this point, no one knows where AI will go in the next 10-20 years, all we can do is wait and see.

Just For Fun
by Bryan Stetser

Across the web, there’s plenty of information, services, and interesting things to explore and mess around with using your browser. If you ever feel bored or want to explore something “old” in a newer platform, try these games out.
Google Chrome has a fun twist on some favorites, all playable without ever leaving the Google search engine.
The first and likely most well known example is called the Dinosaur Game. You may have seen it when your internet has gone down while using Google Chrome. It stars a cute little dinosaur jumping endlessly over cacti for a high score. IF you’d like to try the game out on Chrome, type “chrome://dino” (without parenthesis) into your address bar to launch it.
If you are interested in playing an old arcade classic, typing Pac-Man into the Google search box will let you play a small game of Pac-Man in a unique Google themed playfield.
You can also do the same for other various games like Minesweeper, Tic Tac Toe, Snake Game, and even Solitaire; all you have to do is search them up on Google.
If you type Atari Breakout into Google and click “I’m feeling lucky”, you can experience a recreation of the old Atari classic Breakout, but with Google images instead of bricks.
Google Chrome isn’t the only browser that has exclusive web games. If you are a Microsoft Edge user, typing “edge://surf” into the address bar will let you play a fun little surfing game trying to avoid obstacles and score points.
The next time you feel bored and want to kill some time, try these out and see what you think!

Getting Started Creating a Smart Home
by Bryan Stetser

This week we will continue on about the topic of smart devices. We talked about smart lights last week, and that is only the tip of the smart device iceberg.
One of the main things that attracts people to smart devices is the ability to use Voice Commands. Smart Speakers and Smart Displays are a very popular forms of smart devices for homes, allowing for easy voice communication with other devices. Two examples are the Amazon Echo Show and Google Nest Hub. Earlier generations were simply speakers but quickly advanced into displays.
These devices can be quite flexible in what you can do with them, like scheduling alarms, reminders, and calendar items as well as keeping track of time, playing music, and setting up shopping lists. You can receive news and weather summaries, search for a recipe and even set timers. A very popular feature of these devices include Voice Assistants: Amazon’s Alexa and Google Assistant. Even having just one around your home can be quite helpful.
We started with Amazon Echo devices, so for the purposes of this article, I will reference my smart experiences from that perspective.
Some of the smart devices that I’ve personally tried (aside from lights) are smart plugs, doorbells, TVs, microwaves, and air conditioners. While Amazon has started rolling out their own branded smart devices, any non Amazon device requires its own app to set up initially and then generally can interface with Alexa. Smart devices access your Internet network over the 2.4GHz band of your modem and this can cause some confusion when learning to set up devices. We’ve probably all made the mistake of trying to log a device onto the 5GHz band and been frustrated when it doesn’t work, but the devices are not hard to set up.
Smart devices function the same as their dumb counterparts; you can still manually control them but the ability to use voice commands and scheduling is a huge convenience.
My thoughts on the devices I’ve used vary. I think smart lights are a good introduction to smart technology in the home and I believe a smart doorbell is another good starter device. Smart doorbells allow you to visually see who is outside as well as communicate with them via a 2-way intercom without having to having to actually go to the door to check. Alexa can interface with the doorbell and display the video, but you can also communicate with your visitor over the doorbell’s phone app. This can give the appearance of someone being at home when they actually aren’t. These doorbells can save videos to an SD card, or you can pay a low monthly subscription fee to save the videos online for up to a month.
Smart TVs are fairly common in homes now and are loaded up with extra functionalities. Not only do they come with internet functionality, but they can also support streaming services like Netflix, Amazon Prime, Apple TV, and more. They also likely come with web browsers and YouTube support built in, allowing you to browse the web and even watch videos from YouTube for free. Some even come with services like Samsung TV Plus and Pluto TV which are free ad-supported TV streaming services that allow you to watch shows from a list of various channels if you don’t have an existing cable subscription or Satellite to start with. Some things that I personally do not like about these devices though is that they often have lots of ads placed about depending on the device and they can sometimes be rather slow to start up. It seems to me that streaming services are becoming preferred over expensive cable and satellite packages.
I wasn’t impressed with the smart microwave we decided to add to our kitchen. It was a Sharp microwave and was actually pretty cool. Unfortunately it had a tendency to overheat and shut down. It died after about a year.
Last year we installed a couple of Midea smart air conditioners (window models) and they work great. They do have remotes, but being able to voice control them (on/off, fan speed, temperature) eliminates the need of keeping track of one more remote.
Smart plugs aren’t the most exciting devices out there, but I feel they are worth mentioning and may be a good way to incorporate some smart functionality into your home without having to buy a bunch of smart devices.
Smart plugs are an adapter of sorts; you plug them into your wall outlet and then plug a nonsmart device into them. These can be programmed on schedules as well as voice activated when interfacing with Echo or Google devices. You could plug a lamp with a regular incandescent bulb into a smart plug and use voice commands to turn it on or off, as well as schedule your lamp to be on for certain hours. The same would be true for an old school TV or just about anything you’d want to be able to voice control for an on/off state. Unfortunately, that’s about all smart plugs can do, but they are an inexpensive way to bring some smart technology into your home without spending a lot. They won’t dim or change colors like smart bulbs will, but you can probably find a few handy ways to use them nonetheless. My LED signs at the shop are controlled by smart plugs.
Smart devices are capable of simplifying daily tasks in your life and you can’t beat the convenience. If you’re considering a starting point for trying out smart devices in your home, consider looking into a smart speaker like an Amazon Echo or Google Nest Hub, a smart doorbell like a Ring Doorbell and some smart bulbs and/or plugs, as I have found these devices to be the most useful of the devices I’ve tried. You can create simple or more complex routines beyond just turning your lights on and off. (My mom has an Intruder Alert command that turns the colored bulbs red, announces “resistance is futile” and plays the Imperial March – you’ll have to ask her why. She also has a routine set for the winter months to turn her truck on (which has Alexa capabilities) so the seats and steering wheel warm up before we leave in the morning).
If you are interested in picking up some smart bulbs or plugs for your home, stop by Computers & More of Raton at 800 S 2nd Street, Thursdays and Fridays from 9am – 2pm and let me help you get started.

How Smart is Your Home?
by Bryan Stetser

Technology advancements have brought us to the “smart” age. Probably the most familiar device is the smart phone. There are plenty of devices around that have been smart-ified these days, such as cameras, doorbells, thermostats, and lights. It is possible to fairly easily program these devices, too. Today we will be talking about smart lights.
Smart lights are LED lights which contain a specialized chip equipped with wireless technology, allowing for specific programmed behavior through other smart devices like phones. Depending on the bulb, an Internet connection would be required for WiFi bulbs (with or without a hub which is a device wired to your modem). Smart bulbs use the lower band (2.4 GHz) on your modem and will not work on 5GHz, which is true for all smart devices. WiFi bulbs allow you to control your lights from anywhere you have Internet access. Bluetooth bulbs can be paired to your phone and controlled locally, but you need to be around within 100 feet of the bulb.
Smart bulbs come in a variety of shapes and sizes, from regular bulbs to candelabra to floods. There are also light strips which can be great for indirect lighting or anywhere you don’t have traditional lighting access.
So, what makes smart bulbs so popular? They handle glowing on and off in various ways, are easily programmable for schedules and can be color changing to the user’s preferences (not all bulbs are color changing, so if you buy the less expensive white bulbs, you won’t be able to alter the colors). They can also be dimmed to varying degrees without the requirement of a special dimmer switch.
While you can assign individual bulb behavior, it’s possible to “group” bulbs which allows “global” control; an easy way to turn an entire room of bulbs on or off, or dim them all.
As an aside, smart bulbs do not play nicely with dimmer switches. They will flicker and are really annoying. If you have fixtures on a dimmer switch, my advice is to forego using smart bulbs there.
I believe smart bulbs add a great layer of security to your home as well. While I personally don’t remember the old school light timers, a lot of you do – where you plugged your lamps into timers that turned on and off at set times of the day. While that definitely was a way to make your home look lived in while you were away on vacation, it required individual lamps and there was no way to vary the timers once set. Smart lighting has made those timers obsolete and individual lamps are no longer necessary. Users can program any smart bulb, no matter where it’s located; in a lamp or in the ceiling! You can set multiple schedules to more closely replicate someone being in the home.
Probably the most attractive thing about this technology is the ability to use voice commands (through Amazon Echo devices and Google) to control the lights.
There are few drawbacks to smart lighting. One being relying on having functional internet; if it drops out, you won’t be able to use your WiFi smart lights. However, you can still use the manual switches!
Secondly, the bulbs ALL tend to turn on when power is restored after an outage. Light switches must remain in the “on” position in order for your smart lighting to be accessible and the bulbs don’t seem to remember their last state if they were off during a failure. After a few middle of the night outages, we created a routine where we added all our bulbs to a group called “everything” and now simply tell Alexa to turn “everything” off. The alternative would be having to go into an app and manually turning every bulb off, or telling Alexa to turn each bulb off, one at a time.
Lastly, with the variety of smart bulbs now available, it can be tricky to find which bulbs suit your needs if you like really bright lighting. We have used Philips Hue bulbs for the most part since around 2015. We recently decided to try Amazon smart bulbs but found even at 100%, they are not as bright as Hue bulbs. For regular household lighting, it wouldn’t really be an issue, but we found them inadequate for bedside lamps when reading.
Smart lighting prices have come down in price significantly over the years but they are still relatively expensive bulbs compared to what you are used to paying for incandescents or CFLs. The cost is probably less of an issue when you consider LEDs have a long life in comparison, so that may make the cost negiligible.
I’m planning on a followup article talking about the various smart devices we’ve used in our home and whether we think they are worthwhile.
Computers and More does have a small stock of smart bulbs and plugs we never got around to putting in inventory. If you are interested, visit the shop and lets talk about what smart lighting can do for you.

Make Web Browsing a Breeze
By Bryan Stetser

When it comes to browsing the internet, there are plenty of tips and features to make your experience much smoother. I always like to be able to use shortcuts when I can because I find they are often quicker than using a mouse or touchpad. I think you may find these tips helpful.
Six Handy Shortcuts for Browsers
1) Quickly access the address bar without using a mouse is by pressing Ctrl+L or Alt+D together to jump to it instantly.
2) Do you want a fast way to fill in a website address without typing in the whole URL? Just type in the name of the website, then press Ctrl+Enter or Ctrl+Shift+Enter to automatically add the www and com or net parts of the URL. This combo not only completes the web address, it also takes you to the website. Try this, type “theratonian” (without quotes) in the address bar, then Ctrl+Enter. If you were to just type “theratonian” and hit ENTER, you’d be taken to a page of search results instead.
3) Need to jump to a specific browser tab? You can use Ctrl+Tab or Ctrl+Shift+Tab to cycle forward and backwards between specific tabs. Even better: use Ctrl and any number from the number row or numpad to jump to a specific tab quickly (Ctrl+5 to go to the 5th open browser tab for example). If you need to go straight to the last tab, Ctrl+9 will jump to the last open tab, even if you have more than 9 tabs open.
4) Scroll web pages easily without a mouse (or using keypresses)by using the space bar. Tapping the space bar will quickly scroll down full page chunk. while using space and Shift will go up instead.
5) If you right click on a web page link, you can press the E key to copy it; a much quicker way if you don’t want to go through the context menu. Paste link using CTRL+V.
6) Adjusting browser screen to enlarge or reduce display size can be accomplished quickly by pressing CTRL and tapping + to enlarge your display and pressing CTRL and tapping – to shrink display. You can hold the CTRL down and tap + or – multiple times to continue enlarging or shrinking. If you accidentally zoom in or out too much, pressing Ctrl+0 will reset it back to default.
This isn’t a shortcut, but a cool utility not many people know about …
If you want to easily jot notes from websites or copy text or links without having to switch back and forth to a notepad or WORD, here’s a great alternative that allows you to stay in the browser and access a notepad type accessory.
Open a new tab and type the following into the address bar: “data:text/html, <html contenteditable>” (without the quotes). This will take you to a notepad-like page. While limited in that it doesn’t do anything more than allow you to type or paste plain text items, it is very convenient.
If any of these tips helped you out, feel free to let us know on our Facebook page, as well as share any tips you know of which we might not have known about.

Portable Wireless Thermal Printers
By Bryan Stetser

NOTICE: This article was not paid for or endorsed by HPRT, all opinions and thoughts are the article writers’ own views. This device was purchased with the writers’ own funds.
Brand: HPRT
Features: portable, wireless (Bluetooth), wired (USB-C), rechargeable lithium ion battery included
Ink type: inkless
Paper: thermal in widths 8.3” and 4.3” (supplied with 1 roll of 8.3” x 23 feet)
Price: $99.99
Dimensions: 2.5 x 12.22 x 1.56
Weight: 2.8 lbs
Compatible with: macOS, Windows, iPhones and Android
Paper cost: about $8 per roll for 8.3” width
Recently I’ve been messing around with an interesting printer I decided was worth reviewing. The HPRT MT810, is a thermal printer made by Xiamen Hanin Electronic Technology Co., Ltd which can be setup to work with Android and Apple iPhones, as well as laptops and desktops.
It is impressively portable in size and rechargeable, making it easy to bring along to print on-the-go. This makes it a good choice for people on the move constantly and remote workers such as landscapers, auto detailers and anyone who primarily conducts business outside of an office. This portability can definitely make your productivity more efficient. It would work well as a home printer, too. It uses Bluetooth to print from phones (and tablets) and a USB-C cable for laptops and desktops. The Bluetooth allows for an easy way to print documents, pictures, web pages, and more when you aren’t at home or in the office. The thermal paper is seated within the printer and comes on a roll. No external power supply is required; it recharges the lithium ion batteries using USB. While I haven’t used it a lot as of now, the handful of times I’ve tested it seems to work well.
The setup was pretty straightforward and easy. An app (HerePrint) is required for the wireless print jobs. Wired printing requires a printer driver and the user manual give you the information needed for the driver as well as a QR code to get the App. I did need to do a firmware update after I had installed the app and the Bluetooth connection dropped a couple of times during the setup as well, but has stayed connected during the remainder of my initial testing and followup usage. When powering up the printer later on, the Bluetooth does not automatically connect, but the app has a “connect” button to press which easily re-establishes connectivity to the phone.
All print jobs via Bluetooth must be done through the app. There is an interface for choosing files. For wired printing, this printer will show up in application drop down menus just like any other printer.
If you are looking to print in color, this printer isn’t for you since it only prints in black and white. It’s resolution is not high quality but it does work well for text printing and clip art type images. You wouldn’t want to use it for higher end, professional document printing and it’s really not suitable for photos (even in black and white) – you won’t get a crisp printout, but for everyday printing and to print things like estimates, contracts and invoices, I think road warriors would appreciate this little printer.
The thermal paper sold by the the same company is similar to the thermal receipts most merchants use, however it’s a heavier quality paper. I like that the paper is available in two widths as well.
I did have some difficulty unlatching the cover to access the paper roll and this could also be a challenge for others who have motor issues like I have, and perhaps for individuals with arthritis.
Removing the printout is accomplished by tearing it using its serrated edge. This was a challenge to me as well, getting a clean tear, however I think it’s more a matter of getting used to using this type of cutter.
Overall, for the price I paid for this printer and with some slight quirks aside, I’d say it’s worth the money (around $100 for the printer) for what it is and does. The paper at around $8 per roll is significantly more expensive compared to regular printer paper, and for that reason I wouldn’t recommend this printer for large print jobs. On the other hand, this paper uses no ink, so that may offset the paper cost somewhat. I personally will be using it for printing my business documents at the shop.
If you are interested in this grab-and-go printer for your own use, Computers and More of Raton has a few in stock. If you’d like to check it out, feel free to drop on by 800 S 2nd Street to take a look. I’m open Thursday and Friday from 9 AM to 2 PM. You may also call me at 505-990-0128 for more information.

What’s In Those NFC Tags and How Do They Work?
By Bryan Stetser
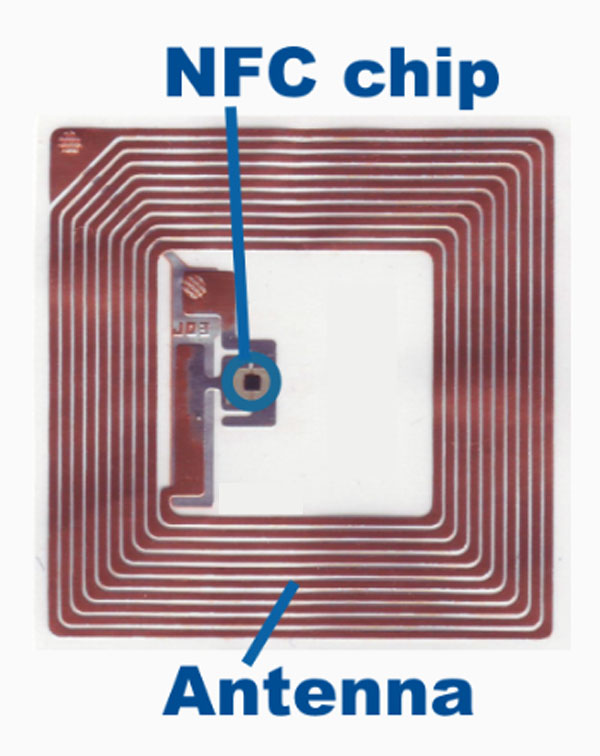
This week we will be continuing on the topic of NFC tags, doing a deeper dive into how these devices function.
For clarification, NFC tags (Near-Field Communication) are tags that contain small amounts of data that can be transferred to other devices like phones or some kind of reader for example.
While most newer Android and Apple phones come with built in NFC support now, it wasn’t always the case. While Android devices started supporting it around 2011, Apple iPhones didn’t start until the iPhone 6. Beginning with iPhone 7, an app was required. With the release of the iPhone XR and XS, no app is required.
NFC tags consist of a radio chip to store data and an antenna to transmit the data. Powered by electromagnetic induction, the tag reader energizes the chip which allows the transfer of data from the tag. These tags must be in close proximity to the receiving device in order to properly work (the exact spot where a device scans NFC tags differs accordingly, so when you first start using your phone to scan tags, you may have to experiment a bit to find the spot where the reader will “see” the tag).
Various use cases such as Tap to Pay for buying products, digital business cards, sending emails, activating routines like timers, alarms, controlling smart devices and so on are just some of the things you can do with NFC tags.
These tags can also be configured to be read-only (once you write data to it, you can’t write to it again) or to be rewritable (up to around 100,000 times). The benefit of course to a rewritable tag is the ability to repurpose it. You can always set a rewritable tag to be “blocked”, making it read-only but once blocked, you cannot make it writable again later on. Tags can also be passworded.
Depending on the tag, they last between 10 to 50 years. They tend to be rather small in size for storage consideration, holding between 96 to 512 bytes. Tags with smaller capacities might really only be suitable for storing a referral link, such as a website address; and not really suitable for a digital business card which would contain significantly more data. (I can help you determine which size tag is suitable for your needs depending on the amount of data you wish to store).
A common question is “are NFC and RFID (Radio Frequency Identification) the same?”. Yes and no. Both use chips and antennas, both transmit data, but RFID transmits data over longer distances than NFC.
NFC allows an individual to decide who to share their information with. Storing your information on an RFID chip would allow someone 10 or 20 feet away with an RFID reader to be able to access your information with no action on your part to share it.
Smartphones are not equipped to read RFID.
Like most modern technology, NFC tags can be susceptible to hackers which is why it’s important to keep device security software up to date. On the upside, tags aren’t easy to hack.
Computers and More of Raton will be rolling out a line of NFC products in the coming weeks. Visit the shop and let’s talk about what NFC can do for you! Please keep an eye on this column for updates about our NFC offerings.

What is NFC?
By Bryan Stetser

With so many various advancements in technology going on these days, today we’ll be talking about this interesting method which allows devices to communicate with others fairly effortlessly.
NFC (Near Field Communication) is not actually a recent technology. If you’ve used Tap To Pay on your phone, that’s NFC. Android phones have had NFC capabilities for years; Apple is a little newer to the party.
This technology is not just for businesses, either. It’s been working its way into becoming widely used by individuals due to its simplicity and availability.
NFC “tags” can be programmed to do a variety of things. A really popular use of NFC for individuals is the Digital Business Card. This can completely eliminate the need for paper business cards although you’d probably want to keep some paper cards on hand for people who don’t utilize NFC technology.
Other tasks NFC can accomplish are things like turning on or off electronics if you have a smart home, allowing a device to connect to your WiFi (without giving out your password), and visiting your social media or website. You could even have a tag on your washing machine to tap, setting a timer to remind you when the load is done and ready to be moved to the dryer!
Once programmed, the information contained on the tag can be transmitted to another device by simply tapping on the tag. These tags don’t store large amounts of data. Data in text format doesn’t require much space, but a video does. While a tag can’t store a video, it can store a link to where the video resides online. Tags also can’t multitask; each tag performs one specific task.
NFC tags can have their downsides though, the fact that they can be so specifically programmed means someone could potentially do something malicious, so use discretion when deciding whether or not to tap a tag. Just as you are careful about phone calls as well as emails with potentially malicious links, you should exercise the same caution with NFC tags. With that warning aside, NFC can come quite in handy and integrating it into your lifestyle might be just for you.
Computers and More of Raton is excited to announce NFC products! If you are interested in a digital business card, please visit the shop to talk about your needs. If you have looked into digital business cards but don’t want to get into subscription hosting of your information, you can completely bypass that expense and I’ll show you how.
I’ll be offering more soon, including items for at-risk individuals and will announce them here in upcoming articles as well as on our Facebook page.
NEXT WEEK:
A geek article on how NFC actually works; what’s in those tags???

How to Take Screenshots on your PC
By Bryan Stetser

As you browse around the internet, you might stumble across something on your screen that you want to take a picture of for future usage. There are several options available in Windows for taking screenshots.
PrtScn Key: The quickest and easiest way to take a screenshot of you entire screen is to press the print screen key, labeled as PrtScn (this key may be labeled with SysRq as well, but as long as it has PrtScn on it, you’re good to go). This will quickly save a picture of your computer screen to your clipboard, and from there you paste into a new image using any photo editing software such as Photoshop or Paint and from there you can edit it.
Windows + PrtScn Keys: If you want to save your screenshot directly to a file, hold down the Windows key and tap the PrtScn key. The file will be stored in your Pictures folder, in a sub-folder named Screenshots. Each file stored here will be named Screenshot (xx) with a sequential numerical value as the (xx).
No PrtScn Key? No problem! Here’s a workaround …
Fn + Windows + Space Bar: This combo will take a screenshot of your entire screen and save it as a file to your Pictures/Screenshots folder as described above.
Alt + PrtScn: If you only want to take a screenshot of the current active window you have open such as a browser, pressing Alt+PrtScn will take a screenshot of the current open window. This will copy the screenshot to the clipboard and from there you will have to use image editing software to save it to a file (as described above) – this method will not save directly to a file.I
Snip & Sketch
Snip & Sketch is a great tool that makes taking and working with screenshots pretty painless. You can launch it from the the Start Menu or run it on demand by using the Shift + Windows + S key combo.
It not only has options for screenshots of your current active window or screen, but it also allows you to write on, highlight, crop and share your screenshots. In Windows 10, Snip and Sketch copies your screenshots to the clipboard and you will have to save it to a file manually. In Windows 11, the snipping tool is similar, except it saves the screenshots to your Pictures/Screenshot folder instead of to your clipboard.
Snip & Sketch has an onscreen menu which lets you select how you want to take a screenshot – eliminating the need to remember which key combos I wrote about earlier in this article do what. The four snip options are: rectangular, freeform, window and full screen. This tool is so versatile, you’ll likely want to use it for all your screenshot needs.
Pro Tip: If you really want to simplify your tasks – you can map your PrtScn key to launch Snip & Sketch. The following instructions will allow you to do the remapping.
Go to SETTINGS
1) Select EASE OF ACCESS (Windows 10) or ACCESSIBILITY (Windows 11)
2) On left menu, scroll down and select KEYBOARD
3) On right menu, scroll to Print Screen shortcut
Under “Use the PrtScn button to open screen snipping”, click the toggle to ON.
4) Toggle to enable
Your PrtScn key will now open the Snip Tool on demand. Of note, it will no longer function as the way to screenshot the entire screen since it was remapped, you’ll have to do that through Snip.
Feel free to keep these tips in mind the next time you need to snap a screenshot of something important on your computer. If you need help with using these key combos, Snip & Sketch or remapping your PrtScn key, please stop by the shop Thursdays or Fridays between 9am – 2pm and I’ll be happy to help you.

Does Your Desktop Computer Need a Maid?
By Bryan Stetser

As we went over tips on how to properly clean your laptop devices last week, this week we will go over properly cleaning and maintaining desktop PCs along with the various peripherals that go along with it.
Once again before you start, it is important to turn off and unplug your desktop computer before you begin cleaning it, but also make sure that you aren’t statically charged when touching it, especially when you open up the computer to clean it. You can do this by touching something metal before touching your computer. but it really is worthwhile to invest in an anti-static device available online.
Open up your pc by removing the side panel or case, depending on the style. Typically the side panel will just slide off, full cases are usually secured with screws and most always on the back of the unit.
If there are any dust filters inside that look particularly dusty, make sure to remove and clean them. Once you do that, take a can of compressed air and carefully spray (short bursts) around areas where you notice dust buildup, like your computer fans. If it’s really dusty inside, you might consider temporarily unplugging certain components if you have trouble cleaning them normally. If you have glass panels on the side that look noticeably fogged up or dirty, feel free to clean them down with wet wipes or paper towels.
If you still notice certain spots with excess dust like the back fans on your computer, it can also be helpful to use cotton swabs and rubbing alcohol to finish the job. A fan style paint brush is also handy to use. Once you are done, reset anything you may have unplugged, plug your PC back in, turn it on, and make sure that everything works.
For external keyboards, a fan or other style paint brush is useful for sweeping away loose dust and debris. You may also use compressed air. As with laptops, sticky or keys that are difficult to depress can also be cleaned similarly by gently flicking off the key covers; use your fingernail or other flat object under a corner and lift. To replace key covers, sit them back over the key and press down gently till they click back into place. For mice, wipe off exterior dust and debris with a microfiber cloth, or paper towel (slightly damp). If your mouse has a trackball, manually remove the trackball to clean the cavity the ball sits in. Most trackball style mice have an opening on the underside which allows you poke a pencil (using eraser end) through to pop the ball out. Others may have a circular disk around the ball to remove in order to get the ball out. Clean the ball with with a gentle soap if it’s grimy from dirt and body oils, dry well. The contacts the ball moves over typically will always have a buildup of dusty debris. You can usually just use your fingernail to dislodge this debris. If needed, use a slightly damp q-tip, dry off the contacts and replace the ball. (You’d be surprised at how often a misbehaving trackball mouse just needs to have its contacts cleaned.) Of note, mousepads contribute a fair amount of debris to to contacts. Once a year, change the battery if your mouse has one.
While you don’t have to clean every single day, it does help to do a routine cleaning session at least every 6 months or so. The longer you keep your computer clean, the healthier your investment will be in the long run.

Does Your Laptop Need a Maid?
By Bryan Stetser

As computer technology advances and can continue to be expensive depending on what you choose in the way of equipment, it becomes even more important to take care of your investment to help it serve you for as long as possible. Housecleaning is not just for your home, and even the most well-kept home doesn’t automatically mean a computer will be as well.
With laptops especially, the last thing you want is to be shelling money out earlier than expected because your device died from poor care. The following are recommended as routine tasks; when your laptop starts looking like it needs some TLC.
A good first start (after you turn off and unplug your device) is to take a can of compressed air and blow around the laptop, like open vents, the side ports, and keyboard area to get out at the dust and grime. Just make sure to avoid shaking the can of compressed air and holding it properly (reasonably upright) to reduce the chance of spraying liquid. Also use short bursts of air.
The next step is to wipe your laptop down to get rid of fingerprints and debris left behind. Microfiber cloths work very well. While some suggest using isopropyl alcohol or a mix of alcohol and water, I find that distilled water works better with cleaning screens. This also takes the guesswork out of whether alcohol is actually safe for your screen. Dab a few drops (never pour liquid directly onto any part of your device) on the microfiber cloth before you clean. Get between and around those keys!
The last thing of note is that at least once a year, it is worth opening the laptop up and directly blowing compressed air around the heatsinks and fans to take care of accumulated dust build up that you can’t easily get to from the outside, particularly if your laptop has a fan. Computer fans continuously suck air in and across the components to reduce heat buildup, so even if your home or work area is spotlessly clean, dust and debris will get in. If you use your laptop on your bed, eat while using it, have furry pets, or live in a dusty environment, this is really important maintenance. It’s always better to get into the habit of taking care of your laptop today so you don’t have to worry about forking over money for a replacement tomorrow and housekeeping is one way to help prevent premature failure.
A word about laptop keyboards: I sometimes have customers bringing in a laptop with a broken keyboard…usually a sticking key, or keys that don’t fully depress or otherwise work. Laptop keyboard failure is pretty uncommon from normal use/wear & tear. Chances are there is some grime (causing stickiness) or debris (causing incomplete depression) under a key or keys. It’s easy to remove the plastic key covers to inspect what may be under the cover. With your device off and unplugged simply slide your fingernail or similar thin flat object under one corner of the key cover and gently flick it up and off. You’ll probably immediately see what is causing the issue. Use compressed air to blow off debris and a damp cloth or Q-Tip to remove any residue. Replace the key cover by gently pressing it back in place. If your keyboard issue isn’t resolved, or you need help with cleaning tasks, stop by the shop to talk about your needs!
Next week, I’ll share tips on taking care of desktop computers.

PC Keyboard Shortcuts to Speed Up Your Productivity
by Bryan Stetser

Hello once again my fellow readers. I’ve been noticing the positive attention my recent Function Keys articles have received and decided to make a follow-up, this time focusing on other helpful Keyboard Shortcuts. Knowing and using these can really speed up your progress. The shortcuts are deployed by simultaneously pressing keys.
CTRL+C – copies whatever you have highlighted with your mouse, this can be text and images
CTRL+V – pastes whatever you have copied into any valid text box on the web, desktop, or even files, too
CTRL+S – comes in handy when you want to save something, and is commonly used on web browsers and for documents
ALT+F – a quick method for opening up a file menu in an application
CTRL+O – opens files in applications or the file explorer
ALT+E – opens the Edit Menu in applications
ALT+TAB – holding down the ALT key and then pressing TAB will shift through the open applications on your task bar without having to click on each. Releasing both keys on the highlighted application will open it
CTRL+TAB – in applications such as WORD or your browser, this combo will scroll through and display each current open document or web page page.
CTRL+N – allows for one to quickly open up a new (blank) file in various applications
CTRL+X – is a great alternative for cutting highlighted text quickly
CTRL+Z – this combo will save you the regret of having used CTRL+X when you shouldn’t have. CTRL+Z undoes the last action performed in many applications. Some applications also allow this combo to perform multiple “undos”. This shortcut might well become your new best friend.
These are my favorite and most used shortcuts. Keep an eye out for future articles talking about more shortcuts.

Paypal Scam
By Guest Contributor (Bryan’s taking the week off)
A friend (from here on referred to as “Chris”) recently set up a Donation link utilizing a scannable QR Code with Paypal processing collection and distribution of the monies received.
Having received two fairly large transactions through the QR Code almost immediately, Chris noted when logging into the Paypal dashboard that both were on hold. There was no explanation as to why. A written query made to Paypal received a response that the hold was due the to large amounts and could take three weeks to be released.
There is no easy way to contact a live human at Paypal; you can click links on its site for information regarding issues, but you get sent to a Help Center which is nothing more that answers to your query, and nothing more about how to resolve issues. I suggested posting to Paypal’s Facebook page. Paypal does not allow the public to post directly to their Facebook page, so people seeking solutions to their unresolved issues will post comments and questions under existing posts made by Paypal. Agents are typically very responsive to complaints. While they usually send you a link to the Help Center and stuff you’ve probably already read, you may find actual help available if you are persistent in your expectation of resolution beyond reading some help files.
Chris posted on the Facebook page and did receive a response, directed to the help files. However, the next day, Chris received a text message from a representative of Paypal named “Mark” advising he was going to help resolve the issue and the money would be available the next day! After quite some time on the phone, and while acutely aware of how scammers work, Chris realized too late and after providing some sensitive information that “Mark” was indeed a scammer.
Damage control was swift; luckily Chris did not lose any money and was able to safeguard accounts before the scammer gained access to anything. The scammer persisted by calling again the following day, which prompted Chris to tell “Mark” he was a scammer and to not make any future contact.
Here’s the takeaway from Chris’ story:
– Is Paypal’s Facebook page a viable last ditch effort at getting help when it is the only place where you can interact fairly quickly with a human? YES, it is. As Paypal and other large companies make it harder and harder to contact them directly for resolution (most initial responses and “chats” on websites, as well as Facebook are literally all AI), it seems Facebook is the last option left to actually get to a conversation with a live human being. While these agents on Facebook company pages are just that – agents, they can also assist in getting your issue addressed.
– Was “Mark” an actual Paypal representative? NO, he is a scumbag scammer who found another way to exploit decent people, trolling Paypal’s Facebook page for individuals with issues and then doing a little extra work to find out their contact info and using it to get in touch with them.
Due to the timing of a rather fast response from “Mark”, Chris truly thought it was Paypal reaching out because his text message addressed Chris by name, indicated it was Paypal Support and Mark identified as a Supervisor. Chris was frustrated by Paypal’s hold on the money and not being able to get in touch with anyone to address the issue to Chris’ satisfaction. With that in mind, this didn’t seem like a random scammer to Chris.
– If a Paypal agent on Facebook was going to respond privately to a post, they would have done so through Messenger (assuming the poster has Messenger) or first asked the poster to send them a Private Message with details on the issue. Using Messenger in conjunction with a post you have made allows you to determine if you are in fact communicating with someone legitimately representing the page you posted to.
– If you ever receive a phone call or text from someone reporting to be from a company you are trying to contact, especially if the caller ID had no identifying information, ask to call them back. Odds are if Chris had googled the scammer’s number, no information connecting it to Paypal would have come up. I googled and there was NO information connecting this number to any company or person – a number with no company information footprint is likely a scammer.
– Keep your personal info on Facebook private, including the city you live in, email address and phone numbers. Back when Facebook was truly a tool for social connections, it is now a playground for scammers. While Chris’ personal profile (which contains no private information viewable to the public) posted to Paypal’s Facebook page, Chris’ business profile is visible on the personal profile. The scammer clicked over to the business profile and found Chris’ cell number there. This scammer just happened to be one who made a bit of effort.
While there is no way to 100% protect yourself from exposure to scammers, do your best to keep as much of your personal info private and verify anyone who contacts you before engaging even if it seems like legitimate contact.
Unfortunately for Chris, nearly a week later, there is still a hold on the money.
I posted to Paypal’s Facebook Page (see image below) to alert others about “Mark” including his phone number. Paypal did respond saying it is best to contact them directly when this happens using this link: https://www.paypal.com/cshelp/article/HELP165
At the time this was published, they had not responded to my query as to whether sending scammer info to them is then used to alert the public on their Facebook or Website.
Please remember to be kind to the agents you communicate with in business chats, via phone, email and on Facebook. I have always found them to be diligent, respectful and good people. They don’t make company policies, but they do their very best to help resolve issues.
If you need assistance securing your Facebook Page, visit Bryan at Computers and More of Raton for help.
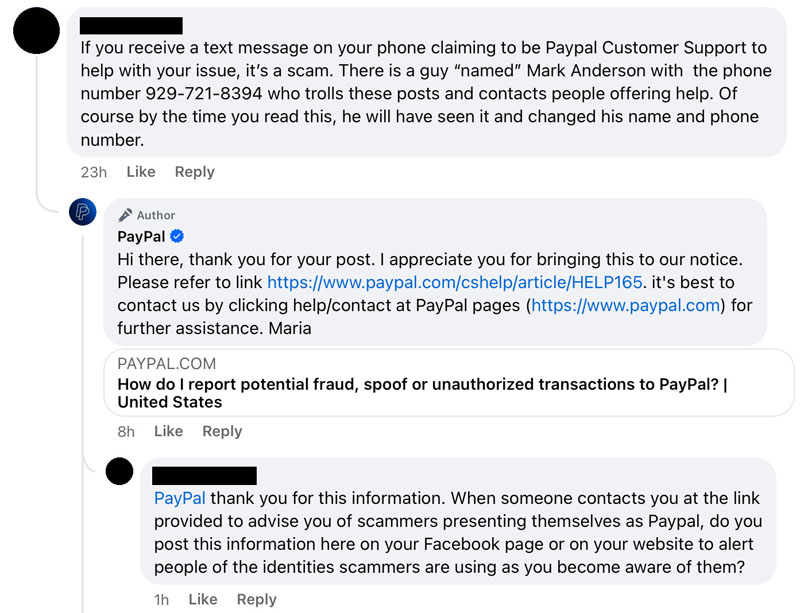

What are Those F Keys For, Anyway?
By Bryan Stetser
Keyboards serve as one of two peripherals used to interact with a computer. Not only can you use a keyboard for plain old typing, this device can also be surprisingly flexible in its functionality. Keys that many people wonder about and can come in handy are the Function Keys. This row of keys is typically located at the very top of the keyboard and the keycaps are labeled from F1 all the way to F12.
These special keys can serve various unique functions depending on what operating system is being run. For the sake of this article, we’ll stick to what they do in Windows. There are some variations as well in how the keys work depending on the keyboard itself; whether you are using a desktop keyboard or one built into a laptop.I’ll talk about general functions on keys simply labeled as F1, F2, F3, F4 first.

When you press F1 using Windows, it will usually open up a HELP prompt or window for the specific program you are using. This doesn’t work for all programs, however, but is worth a try before searching around online for help. On the desktop itself, F1 should take you to the Windows HELP files.
The F2 key is helpful to quickly rename a file, folder or icon if you would rather not be clicking around with the mouse to do so. Just click on what you want to rename once so it is highlighted, hit F2 and you can then type in the new name. Hit Enter to save.
The F3 key can be an extremely helpful search function within applications and especially in browsers when you are dealing with lengthy pages of information and want to find something without scrolling and reading everything again. You would simply use your F3 key, and type in the word or words you are looking for and the browser should highlight your search terms and jump to that section of the page.
The last Function Key today is the F4. In Windows 10, it seems to mostly function as a way to jump to the address bar in your browser or file manage unless used in combination with the CTRL or ALT key, which then allows it to close programs.

Laptop Functions Keys may or may not work by just pressing them. Your keyboard may have a key labeled Fn (usually near shift and CTRL and ALT keys, see image above left) that you may need to press and hold while tapping a particular function key.
Likewise, your Functions Keys may also be labeled with small symbols and can execute other tasks as well. Some labels are self explanatory, others may take a bit of detective work to figure out (or you can reference your owners manual).
Typically, you will press and hold either the CTRL or ALT key while tapping a Function Key to have it perform its secondary function. Looking at the graphic (above right), if you wanted to make your monitor display a little less bright, you would hold down either CTRL or ALT key and tap the F4 key. It should be noted that not all keyboards are labeled exactly as the one above.
As a reminder, not all Function Keys work the same in all programs or all versions of Windows. On laptops, Function Key shortcuts are especially helpful when you don’t have a mouse and rely on a touchscreen which can be cumbersome at times. If you need help figuring out F keys, stop by the shop for a visit!
Next week we will continue going over the various functions of the specific f-keys starting at F5.
What are Those F Keys for, Anyway? … PART 2
Hello again, today we will be continuing on from last week’s article and talking about the function keys from F5 to F8.
The F5 key is useful as a quick and easy way to refresh browser pages. This is especially helpful if you are browsing a page that frequently updates and saves you the trouble of having to scroll all the way back up to the top for new content. Other uses are to refresh the list of items in a folder (although this didn’t work for me), and starting PowerPoint slide shows.
The F6 key, will automatically move the mouse cursor to the browser address bar in Firefox and most other, but not all browsers.
The F7 key is a quick way to open up spell and grammar checking in Microsoft Word and Outlook, as well as enabling Caret Browsing in browsers.
What’s Caret Browsing, you ask? It is the ability to navigate browser pages strictly using the keyboard’s direction arrows. If you’ve ever tried to navigate a website without a mouse, touchpad or touchscreen, you’ll appreciate Caret Browsing. The Chrome browser also includes extensions which enable voice commands to browse, so by enabling those, you don’t even need to touch your keyboard. It does take a bit of practice and for most, using a mouse or touchpad or touchscreen is probably faster, but in a pinch, Caret Browsing and voice browsing are handy!
F7 will also open the Layers menu in Adobe Photoshop.
The F8 key, allows you to access the Windows startup menu while booting up, allowing you to pick from various options like booting into Safe Mode. Safe Mode can help with diagnosing issues and loads your Windows operating system with the bare minimum of drivers.
On some computers, F8 also allows for accessing the Windows recovery system, although your computer may require the use of your installation media to do so.
It’s probably best to not experiment with your F8 key unless you really know your way around this part of Windows. The wrong set of key strokes could brick your computer (turn it into a paperweight) if something is going on with your device and you have your Windows install media.
Keep an eye on this column next week when we finish up the last remaining function keys.
What are Those F Keys For, Anyway? … Part 3
Welcome back, in this article we will finish up going through the remaining function keys, starting at F9 and ending with F12.
The F9 key is useful if you happen to be using Microsoft Word or Excel, since you can easily refresh documents or recalculate spreadsheets. It can also be helpful with as a shortcut for receiving and sending email when using Microsoft Outlook.
With the F10 key, pressing it can be a quick way to open up the menu bar of any application that you have open, as well as being a good substitute for right clicking on a computer mouse if you press F10 + Shift.
If you need a quick method to enter in full screen, pressing F11 will normally put your device into full screen mode instantly, as well as going back to normal if you press if again.
Last but not least, the F12 key can serve a variety of functions, like opening up the developer console on browsers, as well as quickly opening up the Save As tab in Microsoft Word. You can also get to the print menu if you combine F12+ Shift+Ctrl.
I hope you enjoyed a review of the various function keys and maybe have even found some useful. If you would like to refresh yourself on the other Function keys, check out check out Parts 1 and 2 of this article above.
I’ll be adding more Keyboard Shortcut tips in the future!

Google Docs Phishing Scam
By Bryan Stetser
Every passing day, some new form of scam or cyberattack pops up online. This time, we’ll be talking about another variant of malicious phishing emails that can show up in your inbox; the Google Docs Phishing Scam.
Phishing /fishing/ is the practice of sending communications via email or other message platforms in order to fraudulently obtain personal information from the recipient, such as logins and passwords or credit card info
(My mom received the email in this accompanying image a few days ago and had not previously heard about scams related to Google Docs. She also doesn’t know anyone named Yvette, so that was a red flag for her. Typically these scammers are a bit more sophisticated and use either a friend or business name to trick the recipient into believing it’s a legitimate matter.)
These emails look like a regular messages asking you to click on a specific link to edit a document, but instead takes you to a realistically recreated version of the Google website and asks you to login. If you do what this sketchy site says and enter your login info, you will have just given away your Google account information to the scammers behind this scam, providing them with free access to all information stored and associated with your account.
A good way to safeguard against this scam is to be cautious about clicking on Google Doc links unless you know who exactly is sending it. It would be unusual for a friend or business to send a link such as this without including something to indicate what the document is for. If you do click on the document link, you could check the URL or login page for any potential misspellings or signs of something looking weird.
Most importantly, make sure you are always using some form of two-factor authentication* as a safeguard for your account, so even if you do fall victim of a phishing scam, the scammer would still need the code or some other verification to get into your account.
A good rule of thumb to remember with these scams is that if you aren’t familiar with who sent you a message or something feels off, be hesitant before you click on the link. If you need help with setting up two-factor authentication, please visit me at the shop for assistance!
*Two-factor authentication is a 2-step method of keeping your accounts secure. The first factor is your password. The second factor would be a text, email or phone call to you with a code that must also be entered in order to complete the login.

Remote Access Software
By Bryan Stetser
As we move past the craze of the 2020 pandemic, it is still important to bring up a powerful tool that continues to see common use: Remote Access software. TeamViewer, Anydesk, and RemotePC (to name a few) are tools which can allow one to remotely access another computer via means of an Internet connection.
When used properly, said software can allow for users to access and work on a device that might not be easily accessible, or used if one wanted to quickly check up on another computer without having to be physically sitting at the computer. Both computers need to have the software installed and be running it.
There are various jobs that can be accomplished through these programs, allowing for the possibility to partially or fully work remotely. Remote access software can be a powerful productivity tool for legitimate purposes, and it isn’t dangerous on its own.
It can, however present some hefty problems for casual users and some things should be taken into consideration before deciding to use it. One of the biggest concerns is that scammers tend to use this software a lot.
Once a connection is open between yours and a remote computer, the user of the remote computer can see everything on your computer (private information, account data and passwords) and operate it just as if they were sitting at your computer (including logging into any accounts where you have saved passwords for easier access).
While you always have to place a certain amount of faith in anyone who works on your computer, it can be especially risky to entrust someone else to remote into your device, especially when it’s someone you don’t know.
A good rule of thumb is that if you run into a virus or site that starts spewing up a bunch of stuff asking you to call a phone number and the first thing they do is ask you is to download some remote access software, unless you know for sure that you are talking with a legitimate company representative or support person, and not some foreign scammers trying to make a quick buck, DON’T DO IT!
Remote access software can be a great tool to accomplish tasks; whether it is used for good or evil is entirely dependent on who is using it. Be careful!

Virtual Private Networks
By Bryan Stetser
While the internet continues to expand and work its way into our daily lives, it is still important to be mindful of how dangerous it can be. Internet security has always been a roller coaster of effectiveness. We’ve long accepted the importance of strong passwords and Anti Virus software. Another useful tool for added security and privacy is a Virtual Private Network or VPN. They are easy to set up and use.
There are a few different reasons people choose to use VPNs. The one situation where I feel using a VPN is essential is when you are using unsecured public WiFi. Unlike your home WiFi which should always require a password to access, public WiFi has no such built in security and as such, your personal data is literally up for grabs.
A VPN is software which encrypts (scrambles) your data then sends it through a private server and delivers it safely to it’s destination. It also masks the IP address of your device and hides your location. Even if intercepted by someone unscrupulous, they would not be able to decipher your data. If you have to transmit any sensitive data over public WiFi, always use a VPN.
There are other reasons people choose to use VPNs and those are usually for privacy. Your internet provider has the ability to see all data sent and received through their servers. While your provider will know you are using a VPN, they will not be able to see what you’re looking at or doing online. VPNs also prevent websites from tracking you.
Sometimes, websites have blocks in place as well as content region blocks. These prevent certain visitors from accessing sites. If you’ve ever been on Facebook, clicked on a video to watch and received notification that your access is not granted for your country, that is a content region block. It may be a site in Europe that doesn’t allow American access. With a VPN, you would be able to use a setting to send your data through a non American server and then see the video.
While VPNs are legal in many places, you should check before setting one up to make sure your country hasn’t outlawed the use of them.
There are many free VPNs available, but as with anything else, you get what you pay for. When choosing a VPN, more expensive doesn’t necessarily mean better. Read reviews, compare pricing, ask friends and family what they use.
Some sites and services might have VPN detection systems in place, and not allow access to VPN users. VPNs can also slow down your access. Even with the downsides, if you feel like you want your internet to have an added layer of security and protect your privacy, consider using a VPN.

Free Productivity Software
By Bryan Stetser
If there is one use that we tend to associate with computers, work usually comes to mind. In the past, programs like Microsoft WORD and WordPad proved rather important when it came to writing up polished looking documents for work and business. However in recent years, things have begun to change with various products starting to move from a model where you pay once and use it for as long as you want, to a recurring subscription service that you have to constantly shell out money for.
WordPad (which had always been bundled as part of Windows) is going through the process of being discontinued by Microsoft; forcing users to seek out alternatives. If you are interested in looking for alternatives but don’t want to fork out money for an MSOffice license, why not try out something like WPS Office or LibreOffice?
WPS Office and LibreOffice are completely free and replicate the MSOffice experience nicely.
While WPS Office is free, since it is developed by a company, there is also a paid Pro version for around 5 to 6 dollars monthly with some added extras like PDF editing and multi device support, as well as getting plenty of consistent updates.
LibreOffice is also 100% free and open source, meaning not only you can download it and use it without needing to pay a cent, but there is an open community of people working to improve and expand on the product, although updates might not always be as consistent as WPS Office.
Both applications offer their own versions of WORD, Excel, and PowerPoint as well as support for PDF editing. WPS Office is available for Windows, Mac, Linux, Android and iOS. LibreOffice is available for Windows, Mac and Linux.
These applications aim for as much compatibility with MSOffice documents as possible, but there might be some cases where a WORD document could look different in WPS Office or LibreOffice, though it’ll likely depend on what kind of documents you write. While they do share plenty of similarities, it is noted to some that the WPS Office’s UI might be more user friendly to newcomers compared to LibreOffice, but since both apps are free, it doesn’t hurt to try and see which you prefer. If you feel as though you’d want to try something different from MSOffice and save money, try out WPS Office and LibreOffice. I think you’ll be pleased at how much is included in these programs and find they will handle your workload just as well as their more expensive counterpart.
If you find one of these alternatives a great money saving option for your needs, consider supporting them by purchasing the Pro version of WPS Office or donating to LibreOffice.
Below are links to visit each site.
WPS Office https://www.wps.com/
LibreOffice https://www.libreoffice.org/discover/libreoffice/



What is RAM?
By Bryan Stetser
Computers continue to get more complex and powerful with the various parts inside playing important roles in daily computing. While back in the day you could pick up a regular old computer (nothing fancy by today’s standards) and do your business work, these days it’s important to know the terms that refer to the parts of your computer in order to make well-informed choices when purchasing your system.
Today we will be going over two parts of the computer which often confuse consumers; the RAM and HDD.
RAM is Random Access Memory, (long flat circuit boards inside your computer that typically plug into the motherboard, although there is also RAM soldered directly onto the motherboard). RAM can be compared to your brains’ short-term memory function. It functions as a method of temporarily storing data from applications you run, essentially requesting that data to be allocated so your application will properly function. RAM is also volatile; if you close the application or the computer shuts down, the RAM gets emptied.
The amount of RAM you’ll need for daily applications might vary from case to case Basic laptops with 4gbs of RAM minimum is generally suitable for the casual user browsing the net, streaming shows or working on Word documents, spreadsheets and the like, although I’d recommend 8gb if your budget allows and you plan on doing more serious work like Photoshop. 16gb of RAM would be recommended to work comfortably doing video editing with a program like Adobe Premiere, or you have some interest in modern gaming. Any less and you might run into slowdown issues if not outright crashes from your device running out of memory. The amount of RAM you can use does go higher than 16gbs, but how much you need ultimately depends on what your workload is.
Drive storage is permanent storage and where your important files like pictures, videos, documents, and applications reside, essentially functioning like the long term memory functions of your brain, remembering important things that can be recalled later down the line. Because it is required to store files for a long period of time, it is considered non volatile as it can retain data even when the computer is turned off. Because permanent data storage requires a lot of space, these drives must hold more data compared to RAM, potentially being able to hold up to Terabytes of storage for long term preservation. How much drive storage you need will depend on your personal habits. Someone who uses the internet for casual browsing and chatting with friends might not need as much storage as someone who routinely downloads or stores lots of photos, videos, documents, apps, etc on their device. Drive storage comes in different forms like HDD (Hard Disk Drives which stores data on a magnetic disk accessed by platters) and SSD (Solid State Drives which use flash memory like RAM does, but in a non volatile way thus allowing for long term storage.)
While it helps to know the difference between the two, it also helps to keep in mind that technology is constantly advancing. Even if you can get away with running Windows 11 with 4gb of RAM and 128gb of storage, you might run into problems as newer versions of Windows and newer versions of software may require more RAM and files may likewise increase in size.
If you feel like your device might be lacking in storage space or RAM, look for options to physically improve and increase the longetivity of your current device or even plan future device purchases with your workflow in mind.
As always, I welcome you to visit me at the shop to talk about what options you might wish to consider!


How to Choose a Flash Drive for Data Storage
By Bryan Stetser
With technology continuing to advance over the years, it has become much easier, cheaper and more convenient to backup and store your data for safe-keeping. Storage options have evolved from tape to floppy disks to CD-ROMS and finally arriving at USB Flash Drives and SD Cards. Like a double edged sword though, there has also been a rise in fake storage devices. How can you tell the difference between legitimate and fake devices, though? My article today will focus on USB Flash Drives since they tend to be the most popular portable devices for data storage.
When shopping for Flash Drives, you really want to pay attention to manufacturer, capacity and price. A good quality, reliable Flash Drive will not be cheap.
Fake storage devices always appear to be good value at a low price. It can be confusing when you look at a list of drives and you may wonder why one company manufactures 1TB drives which cost well over $100 while another company offers 2TB drives for around $30.
It is difficult to produce reliable high capacity flash drives. 1TB is the limit you’d want to consider, assuming it’s from a legitimate manufacturer. You can expect to pay no less than $100 for a reliable 1TB device. Do not consider 2TB drives; reliable manufactures do not produce anything higher than 1TB for regular consumers.
How do fake drives appear to be high capacity? They are actually repurposed low capacity flash drives (usually 32 or 64GB) which have their firmware programmed in a way to report more storage than they actually have when you plug them into your computer. When you start moving data onto the fake drive and it starts running low on storage, it will just quietly write over your data. Say you save 30GB of videos to your drive, and then add another 50GB of videos later. All your videos will appear to be on the drive, but you won’t find out until you go to open your videos and find them corrupted and unable to be opened.
Even if they cost a bit more, I will always recommend you stick to reputable brands of portable storage devices (no matter how big or small the capacity) to ensure you aren’t getting scammed out of your money and lose your valuable data. Samsung, Western Digital, SanDisk, Corsair, Kingston, and Lexar are a few to use.
As the old saying goes, better to be safe than sorry, especially when it comes to data storage. If you need help with your portable data storage, please stop by my shop and let me assist you!
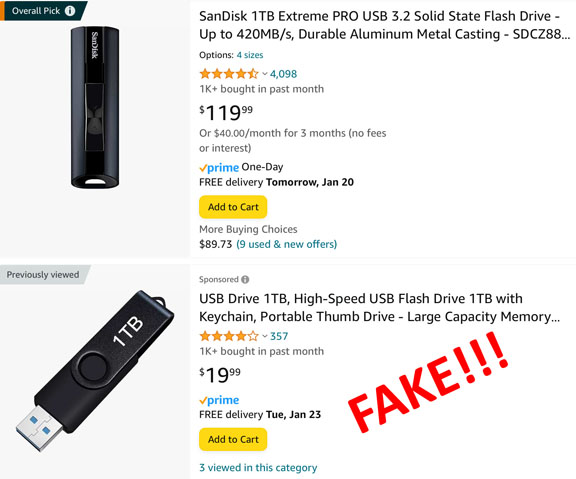


Facebook Video Scams
by Guest Contributor
Recently, a friend of mine in Hawaii posted a video of a car accident on her timeline and I received a notification of the post with her commenting “I can’t believe he is gone: I’m gonna miss him so much”. I immediately recognized this as not being her own post, because these posts have been around for awhile. I texted her to let her know; she said she’d been hearing from lots of friends (because the post had been replicated several times, tagging more friends each time.) She was unable to see it on her timeline to delete it. She had gotten an email earlier from Facebook saying someone from California had logged into her account, so she promptly changed her password. It seems someone was able to get her password somehow. These scams are also occurring on cloned accounts as well.
Scammers recognize people’s empathy over a friends loss as well as wanting more information on who your friend lost and how. They also know you’d not question whether or not the post is legitimate, since it was posted by a friend, someone you trust. The “video” displays a thumbnail image which looks like the scene of a tragedy. There are other variations of these posts as well, but they all have some shock value.
There is NO video. Clicking to play what you believe is a video will take you to the second phase of the scam, being taken to the actual scam website where you can be tricked into different ways of providing personal info or lured into downloading malicious viruses or software.
The takeaway here: if you see your friend posting a shocking video, check with your friend first; don’t click on it!

Is Your Internet Fast Enough?
By Bryan Stetser
January 7, 2024 – While the digital age keeps advancing and improving, so does the need to be constantly connected online. Whether you use the internet for email, banking, watching videos, gaming, to purchase items online, or even indulging in personal hobbies, more people use the internet now than ever.
Having good internet can be a different story though. Some are lucky enough to live in an area with decent to good wired fiber internet, but not everyone has this option. Some people, like those who live in more rural areas, might only have access to satellite as means to connect to the internet, which works at a pretty minimum level. While regular satellite internet options might be passable/below average depending on what you need, if you require something faster to handle situations like online web calls, gaming, streaming, etc., it might be worth looking into Starlink which uses low-orbit satellites.
Recently I upgraded to Starlink from wireless line-of-sight internet. The speed differences are like night and day. While it costs more, if you tend to use the internet for services that require fast consistent speeds, it might be worth checking out services like Starlink.
Prices for Starlink are not cheap. Equipment cost is currently $599 for the dual band modem, dish, and cabling. There is no option to rent this equipment. The cost of monthly service for the standard plan starts at $120 per month with no contracts and 30 days to trial out the service.
In order to obtain service from Starlink, a clear, unobstructed (no trees or buildings in the way) view of the sky is necessary. The dish itself angles about 30° upwards and seems to remain north facing at my home.
There is a Starlink app you can download to help you determine if the service is available in your area and how well it will work for you. It’s very easy to use and if one area of your property doesn’t work, you can repeat the process in different locations. There are several mounting options as well; I started with my dish out in the yard and later had it mounted on top of my dog kennel. The dish also will heat when it detects snow, so you don’t have to go out in the cold to sweep off snow.
The setup itself was easy and straightforward. You get to pick your own modem name and password and the modem boots pretty quickly compared to other modems I’ve used. It defaulted to single band (5GHz) on setup and in order to access 2.4GHz, there is an option in the app to configure that band as well.
I will mention that while the speed of Starlink is very impressive, it does not constantly maintain the exact same download or upload speeds. The actual speed is somewhat variable but is always extremely faster than my old service. I have noticed brief periods where it appears to drop service momentarily as well, but recovers quickly.
My biggest disappointment is the modem does not have an Ethernet port, so out of the box I was unable to hook up devices that require an Ethernet connection (printer, VOIP phone, and a Smart Hub). Starlink does sell an Ethernet adapter ($25) which will provide a single Ethernet port and from there I connected a router to increase port availability. The router cost about $60.
I have been using Starlink for about 3 months now and am very satisfied with its performance. Below is a comparison of speeds between Starlink (left) and my wireless line of sight at the shop (right).
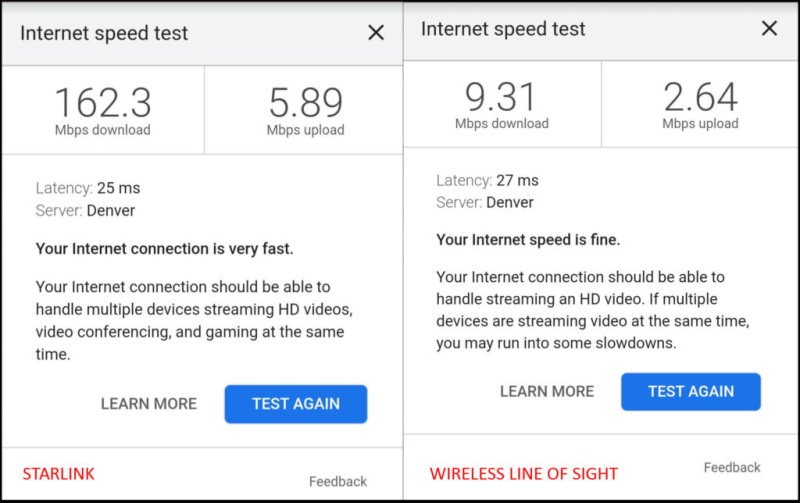

PUT SOME PEP IN YOUR COMPUTER’S STEP
By Bryan Stetser

December 30, 2023. As time marches on, it is inevitable the laptops and computers we purchased years ago might start slowing down or having various issues. While there can be plenty of variables for why an old computer might start slowing down (one example could be running out of storage space), a reasonably common bottleneck could likely be the type of storage drive your device uses.
Older laptops and desktops tend to use HDDs (Hard Disk Drives) to not only handle storage, but also boot Windows. While they are good for long term storage, these drives can eventually start slowing down after years of constant use due to their moving parts. Assuming there are no other issues such as viruses, malware, or corrupted boot files, an aging drive can increase boot times from seconds to even minutes on start up!
If your computer is taking a long time to boot, stop by the shop and I’ll evaluate what could be the cause. If it’s a drive that is worn from time, you might wish to consider upgrading to a Solid State Drive (or SSD for short). Not only do these drives contain no moving parts (meaning a slight bump won’t potentially cause damage and render the drive unreadable), but they are much faster, too. While larger capacity hard disk drives can be cheaper replacements, SSDs have gone down in pricing enough to be really affordable, and most laptops and desktops can accept SSD replacements.
With a bit of technical know-how, you could replace your old hard drive with a fresh new SSD!
If your laptop or desktop starts taking forever to boot and you notice your hard drive sounding like it’s working even when you’re not actively using your computer, a speedy SSD might be the upgrade for you. If you’d rather not do the replacement yourself, Computers & More of Raton can help you find the right SSD for your needs and do the work for you!

Beware – Hackers Pretend to be a Friend Asking for Help
By Bryan Stetser
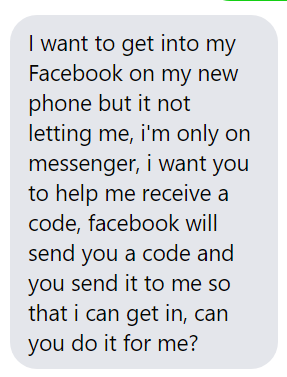
If someone messages you something similar to this, asking for a code to be sent to your phone or email on their behalf, please don’t do it. This is not your friend asking for help, it’s a hacker. A friend of ours has lost access and control of her FB account because someone unknowingly agreed to help thinking it was her asking. These types of messages are not from the account owner.
The Importance of Surge Protectors
By Bryan Stetser

If you have a computer, laptop, or any kind of electronics plugged into an outlet, make sure you are using a fresh surge protector or an Uninterruptable Power Supply (UPS) to safeguard your tech. Surge protectors might protect your devices at first, but they can lose effectiveness over time, especially with lightning strikes. Uninterruptable Power Supplies also function like portable power banks, giving you extra time to shut off your devices safely before the power runs out. Thunderstorms and power blackouts can be especially dangerous if you fail to prep for them. When they happen, your computer could suddenly shut off, risking any unsaved data you had open, or in an even worse case scenario, you risk potential hardware failure from the storm frying your device.
If your computer or laptop isn’t booting after a thunderstorm anymore, bring it down to Computers and More of Raton for an evaluation! If it’s fried, it might still be possible for me to retrieve your data off the drives.

Windows Security Pop Up Scam Ad
By Bryan Stetser
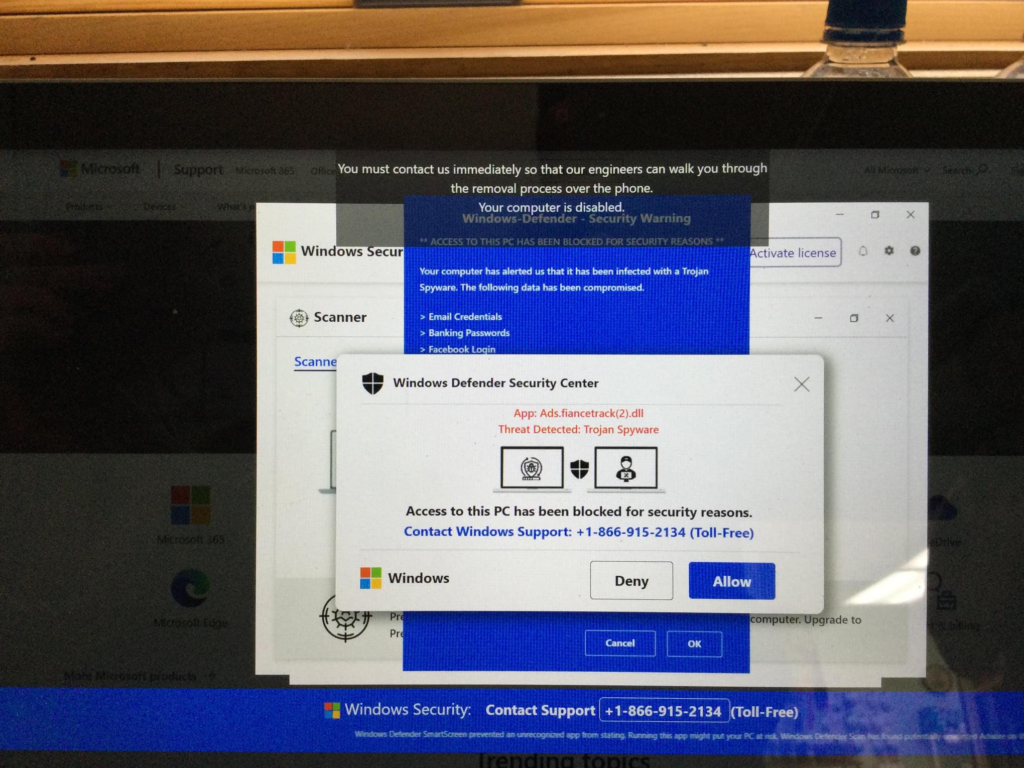
This window opened on my mother’s pc while she was playing a game on Facebook. While you are on the internet, make sure you are aware of the potential dangers of scam ads that try to pretend you PC is in danger and ask you to install or contact throwaway phone numbers. There will be moments where your browser will sometimes be redirected to a fake security warning site that talks about your PC being compromised. If you happen to see something like that while browsing, try to close out of the browser if possible and run Windows Defender, Malwarebytes, or whatever anti-virus software you have on your computer. Under no circumstances should you click on any download links on suspicious pages or call questionable phone numbers for tech support, as they rely on the user being scared enough into doing what they say. Make sure you also pick up ad blocking software like ublock origin, a tool that can block out most ads on the web keeping you safe. Remember to be extremely cautious about letting people remote into your computers as well, as it can be a sure-fire way to lead to questionable people getting access to your private information. Windows Defender will never disable your computer or force you to call a phone number and ask to install remote software to get your computer back into a working state.

Windows 11 and The Future of Computers
By Bryan Stetser

As time marches on, technology will always advance and improve over what we had long ago, such is the case for computers. Microsoft has always been at the forefront of computing, even with it’s competition such as Mac and Linux. However, with Windows 11 coming out very soon, Microsoft has decided to implement a rather strange upgrade policy if you want to upgrade in the first place, by requiring TPM 2.0 support. It is normal for newer operating systems to require newer hardware to run, but Windows 11 is a weird case where even some of the newer computers out there don’t have support for it yet, resulting in Microsoft’s checker app saying they can’t upgrade.
If you are curious about what TPM is, it stands for Trusted Platform Module, a form of device encryption to help protect against malicious attacks against said device and is found on your motherboard. There should be a TPM header spot somewhere that you can slot the 2.0 chip into, which I’d personally recommend doing with a chip that not only has the same pin number and layout of the header, but is also from the same brand as well.
It is possible to install Windows 11 without a TPM 2.0 chip setup, however you’ll be missing out on vital updates and might be at risk of encountering issues according to Microsoft.
TPM chip aside, the other major thing to note is that you’ll need a pretty new processor that came out around 2018-2019 (maybe 2017 in some cases) if you want to have one that meets the minimum requirements. Even with the rather high hardware requirements to attempt upgrading in the first place, most people who have tried the new 11 OS consider it to be average enough or slightly worse when compared to windows 10, with the start bar being shifted to the middle, barely any performance improvement, Microsoft’s aggressive pushing for you to use Edge, and a weird blend of trying to revamp the settings and such while still keeping older stuff around like the control panel. Even with Microsoft planning to cut off Windows 10 support on October 14th 2025, you’ll still be able to use your computer like normal, but security updates and support as such won’t be supplied anymore.
Newer hardware or even certain applications might have a cut off point where you’ll have to either upgrade or be forced to use older or sometimes outdated equipment or applications.
If you still want to bite the bullet for now and upgrade anyway, keep in mind that you’ll need to meet the requirements if you want to take full advantage of the system, which might prove to be an
issue if your computer lacks a TPM 2.0 chip or has an older processor. Even if you meet the requirements and upgrade, you’ll only get a 10 day grace period to test the OS and see if you like it
before Windows auto deletes your Windows 10 files permanently to clear up space. I’d personally recommend waiting awhile before upgrading/buying a new PC, since TPM 2.0 support still seems to be confusing a lot of people with some computers having it and some of them lacking it. Maybe Microsoft will think about lowering some of the requirements later down the line, but on the off chance they decide to stick to it, there will still be newer computers around with Windows 11 available for purchase if you don’t want to mess around with your current computer to get TPM 2.0 setup.
There are also plenty of alternative options if you don’t want to deal with the newer OS’s anymore, such as the Raspberry Pi 4, a smaller computer running the Linux operating system that’s affordable, easy to setup, has no moving parts. You don’t have to worry about ever upgrading hardware or strict hardware requirements or lack of support. Stop by the shop to see what a Raspberry pi is!



