
Bryan Stetser, owner of Computers & More located at 800 S. 2nd Street, in Raton will be providing hints and tips for care and use of your computer or laptop on this page. His shop hours are: 9:00 AM – 2:00 PM Thursday and Friday. Questions or need help? Call Bryan at (505) 990-0128.
Not only does Bryan provide basic PC service and repairs, specializing in software related issues, but he also has some laptops and computer parts, hard drives, and other supplies on hand.
Select from the list below for helpful tech advice:
- How to Take Screenshots on Your PC
- Does Your Desktop Computer Need a Maid
- Does Your Laptop Need a Maid?
- PC Keyboard Shortcuts to Speed Up Your Productivity
- Paypal Scam
- What are those F Keys For, Anyway?
- What are Those F Keys for ,Anyway? PART 2
- What are Those F Keys for, Anyway? PART 3
- Google Docs Phishing Scam
- Remote Access Software
- Virtual Private Networks
- Free Productivity Software
- What is RAM?
- How to Choose a Flash Drive for Data Storage
- Facebook Video Scams
- Is Your Internet Fast Enough?
- Is Your Computer Fast Enough?
- Put Some Pep in Your Computer’s Step
- Beware – Hackers Pretend to be a Friend Asking for Help
- The Importance of Surge Protectors
- Windows Security Pop Up Scam Ad
- Windows 11 and the Future of Computers
How to Take Screenshots on your PC
By Bryan Stetser

As you browse around the internet, you might stumble across something on your screen that you want to take a picture of for future usage. There are several options available in Windows for taking screenshots.
PrtScn Key: The quickest and easiest way to take a screenshot of you entire screen is to press the print screen key, labeled as PrtScn (this key may be labeled with SysRq as well, but as long as it has PrtScn on it, you’re good to go). This will quickly save a picture of your computer screen to your clipboard, and from there you paste into a new image using any photo editing software such as Photoshop or Paint and from there you can edit it.
Windows + PrtScn Keys: If you want to save your screenshot directly to a file, hold down the Windows key and tap the PrtScn key. The file will be stored in your Pictures folder, in a sub-folder named Screenshots. Each file stored here will be named Screenshot (xx) with a sequential numerical value as the (xx).
No PrtScn Key? No problem! Here’s a workaround …
Fn + Windows + Space Bar: This combo will take a screenshot of your entire screen and save it as a file to your Pictures/Screenshots folder as described above.
Alt + PrtScn: If you only want to take a screenshot of the current active window you have open such as a browser, pressing Alt+PrtScn will take a screenshot of the current open window. This will copy the screenshot to the clipboard and from there you will have to use image editing software to save it to a file (as described above) – this method will not save directly to a file.I
Snip & Sketch
Snip & Sketch is a great tool that makes taking and working with screenshots pretty painless. You can launch it from the the Start Menu or run it on demand by using the Shift + Windows + S key combo.
It not only has options for screenshots of your current active window or screen, but it also allows you to write on, highlight, crop and share your screenshots. In Windows 10, Snip and Sketch copies your screenshots to the clipboard and you will have to save it to a file manually. In Windows 11, the snipping tool is similar, except it saves the screenshots to your Pictures/Screenshot folder instead of to your clipboard.
Snip & Sketch has an onscreen menu which lets you select how you want to take a screenshot – eliminating the need to remember which key combos I wrote about earlier in this article do what. The four snip options are: rectangular, freeform, window and full screen. This tool is so versatile, you’ll likely want to use it for all your screenshot needs.
Pro Tip: If you really want to simplify your tasks – you can map your PrtScn key to launch Snip & Sketch. The following instructions will allow you to do the remapping.
Go to SETTINGS
1) Select EASE OF ACCESS (Windows 10) or ACCESSIBILITY (Windows 11)
2) On left menu, scroll down and select KEYBOARD
3) On right menu, scroll to Print Screen shortcut
Under “Use the PrtScn button to open screen snipping”, click the toggle to ON.
4) Toggle to enable
Your PrtScn key will now open the Snip Tool on demand. Of note, it will no longer function as the way to screenshot the entire screen since it was remapped, you’ll have to do that through Snip.
Feel free to keep these tips in mind the next time you need to snap a screenshot of something important on your computer. If you need help with using these key combos, Snip & Sketch or remapping your PrtScn key, please stop by the shop Thursdays or Fridays between 9am – 2pm and I’ll be happy to help you.

Does Your Desktop Computer Need a Maid?
By Bryan Stetser

As we went over tips on how to properly clean your laptop devices last week, this week we will go over properly cleaning and maintaining desktop PCs along with the various peripherals that go along with it.
Once again before you start, it is important to turn off and unplug your desktop computer before you begin cleaning it, but also make sure that you aren’t statically charged when touching it, especially when you open up the computer to clean it. You can do this by touching something metal before touching your computer. but it really is worthwhile to invest in an anti-static device available online.
Open up your pc by removing the side panel or case, depending on the style. Typically the side panel will just slide off, full cases are usually secured with screws and most always on the back of the unit.
If there are any dust filters inside that look particularly dusty, make sure to remove and clean them. Once you do that, take a can of compressed air and carefully spray (short bursts) around areas where you notice dust buildup, like your computer fans. If it’s really dusty inside, you might consider temporarily unplugging certain components if you have trouble cleaning them normally. If you have glass panels on the side that look noticeably fogged up or dirty, feel free to clean them down with wet wipes or paper towels.
If you still notice certain spots with excess dust like the back fans on your computer, it can also be helpful to use cotton swabs and rubbing alcohol to finish the job. A fan style paint brush is also handy to use. Once you are done, reset anything you may have unplugged, plug your PC back in, turn it on, and make sure that everything works.
For external keyboards, a fan or other style paint brush is useful for sweeping away loose dust and debris. You may also use compressed air. As with laptops, sticky or keys that are difficult to depress can also be cleaned similarly by gently flicking off the key covers; use your fingernail or other flat object under a corner and lift. To replace key covers, sit them back over the key and press down gently till they click back into place. For mice, wipe off exterior dust and debris with a microfiber cloth, or paper towel (slightly damp). If your mouse has a trackball, manually remove the trackball to clean the cavity the ball sits in. Most trackball style mice have an opening on the underside which allows you poke a pencil (using eraser end) through to pop the ball out. Others may have a circular disk around the ball to remove in order to get the ball out. Clean the ball with with a gentle soap if it’s grimy from dirt and body oils, dry well. The contacts the ball moves over typically will always have a buildup of dusty debris. You can usually just use your fingernail to dislodge this debris. If needed, use a slightly damp q-tip, dry off the contacts and replace the ball. (You’d be surprised at how often a misbehaving trackball mouse just needs to have its contacts cleaned.) Of note, mousepads contribute a fair amount of debris to to contacts. Once a year, change the battery if your mouse has one.
While you don’t have to clean every single day, it does help to do a routine cleaning session at least every 6 months or so. The longer you keep your computer clean, the healthier your investment will be in the long run.

Does Your Laptop Need a Maid?
By Bryan Stetser

As computer technology advances and can continue to be expensive depending on what you choose in the way of equipment, it becomes even more important to take care of your investment to help it serve you for as long as possible. Housecleaning is not just for your home, and even the most well-kept home doesn’t automatically mean a computer will be as well.
With laptops especially, the last thing you want is to be shelling money out earlier than expected because your device died from poor care. The following are recommended as routine tasks; when your laptop starts looking like it needs some TLC.
A good first start (after you turn off and unplug your device) is to take a can of compressed air and blow around the laptop, like open vents, the side ports, and keyboard area to get out at the dust and grime. Just make sure to avoid shaking the can of compressed air and holding it properly (reasonably upright) to reduce the chance of spraying liquid. Also use short bursts of air.
The next step is to wipe your laptop down to get rid of fingerprints and debris left behind. Microfiber cloths work very well. While some suggest using isopropyl alcohol or a mix of alcohol and water, I find that distilled water works better with cleaning screens. This also takes the guesswork out of whether alcohol is actually safe for your screen. Dab a few drops (never pour liquid directly onto any part of your device) on the microfiber cloth before you clean. Get between and around those keys!
The last thing of note is that at least once a year, it is worth opening the laptop up and directly blowing compressed air around the heatsinks and fans to take care of accumulated dust build up that you can’t easily get to from the outside, particularly if your laptop has a fan. Computer fans continuously suck air in and across the components to reduce heat buildup, so even if your home or work area is spotlessly clean, dust and debris will get in. If you use your laptop on your bed, eat while using it, have furry pets, or live in a dusty environment, this is really important maintenance. It’s always better to get into the habit of taking care of your laptop today so you don’t have to worry about forking over money for a replacement tomorrow and housekeeping is one way to help prevent premature failure.
A word about laptop keyboards: I sometimes have customers bringing in a laptop with a broken keyboard…usually a sticking key, or keys that don’t fully depress or otherwise work. Laptop keyboard failure is pretty uncommon from normal use/wear & tear. Chances are there is some grime (causing stickiness) or debris (causing incomplete depression) under a key or keys. It’s easy to remove the plastic key covers to inspect what may be under the cover. With your device off and unplugged simply slide your fingernail or similar thin flat object under one corner of the key cover and gently flick it up and off. You’ll probably immediately see what is causing the issue. Use compressed air to blow off debris and a damp cloth or Q-Tip to remove any residue. Replace the key cover by gently pressing it back in place. If your keyboard issue isn’t resolved, or you need help with cleaning tasks, stop by the shop to talk about your needs!
Next week, I’ll share tips on taking care of desktop computers.

PC Keyboard Shortcuts to Speed Up Your Productivity
by Bryan Stetser

Hello once again my fellow readers. I’ve been noticing the positive attention my recent Function Keys articles have received and decided to make a follow-up, this time focusing on other helpful Keyboard Shortcuts. Knowing and using these can really speed up your progress. The shortcuts are deployed by simultaneously pressing keys.
CTRL+C – copies whatever you have highlighted with your mouse, this can be text and images
CTRL+V – pastes whatever you have copied into any valid text box on the web, desktop, or even files, too
CTRL+S – comes in handy when you want to save something, and is commonly used on web browsers and for documents
ALT+F – a quick method for opening up a file menu in an application
CTRL+O – opens files in applications or the file explorer
ALT+E – opens the Edit Menu in applications
ALT+TAB – holding down the ALT key and then pressing TAB will shift through the open applications on your task bar without having to click on each. Releasing both keys on the highlighted application will open it
CTRL+TAB – in applications such as WORD or your browser, this combo will scroll through and display each current open document or web page page.
CTRL+N – allows for one to quickly open up a new (blank) file in various applications
CTRL+X – is a great alternative for cutting highlighted text quickly
CTRL+Z – this combo will save you the regret of having used CTRL+X when you shouldn’t have. CTRL+Z undoes the last action performed in many applications. Some applications also allow this combo to perform multiple “undos”. This shortcut might well become your new best friend.
These are my favorite and most used shortcuts. Keep an eye out for future articles talking about more shortcuts.

Paypal Scam
By Guest Contributor (Bryan’s taking the week off)
A friend (from here on referred to as “Chris”) recently set up a Donation link utilizing a scannable QR Code with Paypal processing collection and distribution of the monies received.
Having received two fairly large transactions through the QR Code almost immediately, Chris noted when logging into the Paypal dashboard that both were on hold. There was no explanation as to why. A written query made to Paypal received a response that the hold was due the to large amounts and could take three weeks to be released.
There is no easy way to contact a live human at Paypal; you can click links on its site for information regarding issues, but you get sent to a Help Center which is nothing more that answers to your query, and nothing more about how to resolve issues. I suggested posting to Paypal’s Facebook page. Paypal does not allow the public to post directly to their Facebook page, so people seeking solutions to their unresolved issues will post comments and questions under existing posts made by Paypal. Agents are typically very responsive to complaints. While they usually send you a link to the Help Center and stuff you’ve probably already read, you may find actual help available if you are persistent in your expectation of resolution beyond reading some help files.
Chris posted on the Facebook page and did receive a response, directed to the help files. However, the next day, Chris received a text message from a representative of Paypal named “Mark” advising he was going to help resolve the issue and the money would be available the next day! After quite some time on the phone, and while acutely aware of how scammers work, Chris realized too late and after providing some sensitive information that “Mark” was indeed a scammer.
Damage control was swift; luckily Chris did not lose any money and was able to safeguard accounts before the scammer gained access to anything. The scammer persisted by calling again the following day, which prompted Chris to tell “Mark” he was a scammer and to not make any future contact.
Here’s the takeaway from Chris’ story:
– Is Paypal’s Facebook page a viable last ditch effort at getting help when it is the only place where you can interact fairly quickly with a human? YES, it is. As Paypal and other large companies make it harder and harder to contact them directly for resolution (most initial responses and “chats” on websites, as well as Facebook are literally all AI), it seems Facebook is the last option left to actually get to a conversation with a live human being. While these agents on Facebook company pages are just that – agents, they can also assist in getting your issue addressed.
– Was “Mark” an actual Paypal representative? NO, he is a scumbag scammer who found another way to exploit decent people, trolling Paypal’s Facebook page for individuals with issues and then doing a little extra work to find out their contact info and using it to get in touch with them.
Due to the timing of a rather fast response from “Mark”, Chris truly thought it was Paypal reaching out because his text message addressed Chris by name, indicated it was Paypal Support and Mark identified as a Supervisor. Chris was frustrated by Paypal’s hold on the money and not being able to get in touch with anyone to address the issue to Chris’ satisfaction. With that in mind, this didn’t seem like a random scammer to Chris.
– If a Paypal agent on Facebook was going to respond privately to a post, they would have done so through Messenger (assuming the poster has Messenger) or first asked the poster to send them a Private Message with details on the issue. Using Messenger in conjunction with a post you have made allows you to determine if you are in fact communicating with someone legitimately representing the page you posted to.
– If you ever receive a phone call or text from someone reporting to be from a company you are trying to contact, especially if the caller ID had no identifying information, ask to call them back. Odds are if Chris had googled the scammer’s number, no information connecting it to Paypal would have come up. I googled and there was NO information connecting this number to any company or person – a number with no company information footprint is likely a scammer.
– Keep your personal info on Facebook private, including the city you live in, email address and phone numbers. Back when Facebook was truly a tool for social connections, it is now a playground for scammers. While Chris’ personal profile (which contains no private information viewable to the public) posted to Paypal’s Facebook page, Chris’ business profile is visible on the personal profile. The scammer clicked over to the business profile and found Chris’ cell number there. This scammer just happened to be one who made a bit of effort.
While there is no way to 100% protect yourself from exposure to scammers, do your best to keep as much of your personal info private and verify anyone who contacts you before engaging even if it seems like legitimate contact.
Unfortunately for Chris, nearly a week later, there is still a hold on the money.
I posted to Paypal’s Facebook Page (see image below) to alert others about “Mark” including his phone number. Paypal did respond saying it is best to contact them directly when this happens using this link: https://www.paypal.com/cshelp/article/HELP165
At the time this was published, they had not responded to my query as to whether sending scammer info to them is then used to alert the public on their Facebook or Website.
Please remember to be kind to the agents you communicate with in business chats, via phone, email and on Facebook. I have always found them to be diligent, respectful and good people. They don’t make company policies, but they do their very best to help resolve issues.
If you need assistance securing your Facebook Page, visit Bryan at Computers and More of Raton for help.
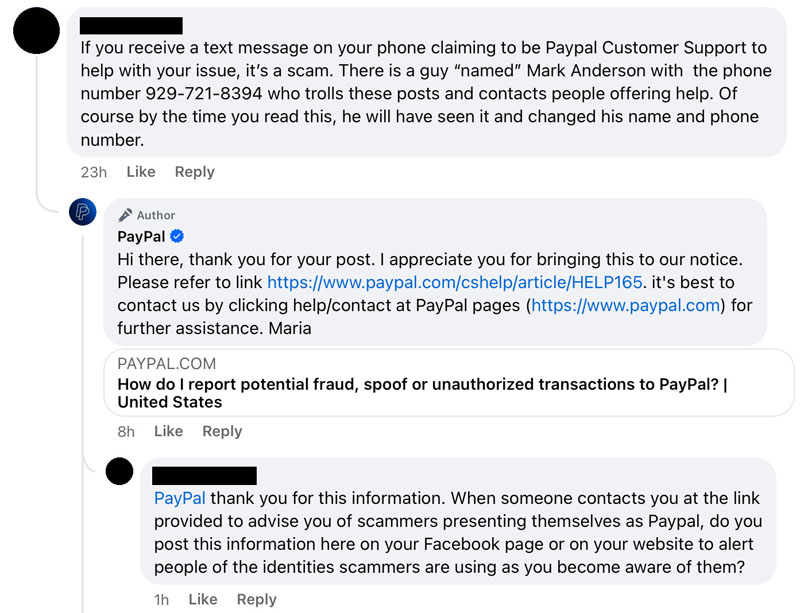

What are Those F Keys For, Anyway?
By Bryan Stetser
Keyboards serve as one of two peripherals used to interact with a computer. Not only can you use a keyboard for plain old typing, this device can also be surprisingly flexible in its functionality. Keys that many people wonder about and can come in handy are the Function Keys. This row of keys is typically located at the very top of the keyboard and the keycaps are labeled from F1 all the way to F12.
These special keys can serve various unique functions depending on what operating system is being run. For the sake of this article, we’ll stick to what they do in Windows. There are some variations as well in how the keys work depending on the keyboard itself; whether you are using a desktop keyboard or one built into a laptop.I’ll talk about general functions on keys simply labeled as F1, F2, F3, F4 first.

When you press F1 using Windows, it will usually open up a HELP prompt or window for the specific program you are using. This doesn’t work for all programs, however, but is worth a try before searching around online for help. On the desktop itself, F1 should take you to the Windows HELP files.
The F2 key is helpful to quickly rename a file, folder or icon if you would rather not be clicking around with the mouse to do so. Just click on what you want to rename once so it is highlighted, hit F2 and you can then type in the new name. Hit Enter to save.
The F3 key can be an extremely helpful search function within applications and especially in browsers when you are dealing with lengthy pages of information and want to find something without scrolling and reading everything again. You would simply use your F3 key, and type in the word or words you are looking for and the browser should highlight your search terms and jump to that section of the page.
The last Function Key today is the F4. In Windows 10, it seems to mostly function as a way to jump to the address bar in your browser or file manage unless used in combination with the CTRL or ALT key, which then allows it to close programs.

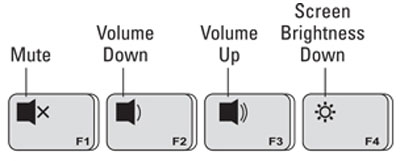
Laptop Functions Keys may or may not work by just pressing them. Your keyboard may have a key labeled Fn (usually near shift and CTRL and ALT keys, see image above left) that you may need to press and hold while tapping a particular function key.
Likewise, your Functions Keys may also be labeled with small symbols and can execute other tasks as well. Some labels are self explanatory, others may take a bit of detective work to figure out (or you can reference your owners manual).
Typically, you will press and hold either the CTRL or ALT key while tapping a Function Key to have it perform its secondary function. Looking at the graphic (above right), if you wanted to make your monitor display a little less bright, you would hold down either CTRL or ALT key and tap the F4 key. It should be noted that not all keyboards are labeled exactly as the one above.
As a reminder, not all Function Keys work the same in all programs or all versions of Windows. On laptops, Function Key shortcuts are especially helpful when you don’t have a mouse and rely on a touchscreen which can be cumbersome at times. If you need help figuring out F keys, stop by the shop for a visit!
Next week we will continue going over the various functions of the specific f-keys starting at F5.
What are Those F Keys for, Anyway? … PART 2
Hello again, today we will be continuing on from last week’s article and talking about the function keys from F5 to F8.
The F5 key is useful as a quick and easy way to refresh browser pages. This is especially helpful if you are browsing a page that frequently updates and saves you the trouble of having to scroll all the way back up to the top for new content. Other uses are to refresh the list of items in a folder (although this didn’t work for me), and starting PowerPoint slide shows.
The F6 key, will automatically move the mouse cursor to the browser address bar in Firefox and most other, but not all browsers.
The F7 key is a quick way to open up spell and grammar checking in Microsoft Word and Outlook, as well as enabling Caret Browsing in browsers.
What’s Caret Browsing, you ask? It is the ability to navigate browser pages strictly using the keyboard’s direction arrows. If you’ve ever tried to navigate a website without a mouse, touchpad or touchscreen, you’ll appreciate Caret Browsing. The Chrome browser also includes extensions which enable voice commands to browse, so by enabling those, you don’t even need to touch your keyboard. It does take a bit of practice and for most, using a mouse or touchpad or touchscreen is probably faster, but in a pinch, Caret Browsing and voice browsing are handy!
F7 will also open the Layers menu in Adobe Photoshop.
The F8 key, allows you to access the Windows startup menu while booting up, allowing you to pick from various options like booting into Safe Mode. Safe Mode can help with diagnosing issues and loads your Windows operating system with the bare minimum of drivers.
On some computers, F8 also allows for accessing the Windows recovery system, although your computer may require the use of your installation media to do so.
It’s probably best to not experiment with your F8 key unless you really know your way around this part of Windows. The wrong set of key strokes could brick your computer (turn it into a paperweight) if something is going on with your device and you have your Windows install media.
Keep an eye on this column next week when we finish up the last remaining function keys.
What are Those F Keys For, Anyway? … Part 3
Welcome back, in this article we will finish up going through the remaining function keys, starting at F9 and ending with F12.
The F9 key is useful if you happen to be using Microsoft Word or Excel, since you can easily refresh documents or recalculate spreadsheets. It can also be helpful with as a shortcut for receiving and sending email when using Microsoft Outlook.
With the F10 key, pressing it can be a quick way to open up the menu bar of any application that you have open, as well as being a good substitute for right clicking on a computer mouse if you press F10 + Shift.
If you need a quick method to enter in full screen, pressing F11 will normally put your device into full screen mode instantly, as well as going back to normal if you press if again.
Last but not least, the F12 key can serve a variety of functions, like opening up the developer console on browsers, as well as quickly opening up the Save As tab in Microsoft Word. You can also get to the print menu if you combine F12+ Shift+Ctrl.
I hope you enjoyed a review of the various function keys and maybe have even found some useful. If you would like to refresh yourself on the other Function keys, check out check out Parts 1 and 2 of this article above.
I’ll be adding more Keyboard Shortcut tips in the future!

Google Docs Phishing Scam
By Bryan Stetser
Every passing day, some new form of scam or cyberattack pops up online. This time, we’ll be talking about another variant of malicious phishing emails that can show up in your inbox; the Google Docs Phishing Scam.
Phishing /fishing/ is the practice of sending communications via email or other message platforms in order to fraudulently obtain personal information from the recipient, such as logins and passwords or credit card info
(My mom received the email in this accompanying image a few days ago and had not previously heard about scams related to Google Docs. She also doesn’t know anyone named Yvette, so that was a red flag for her. Typically these scammers are a bit more sophisticated and use either a friend or business name to trick the recipient into believing it’s a legitimate matter.)
These emails look like a regular messages asking you to click on a specific link to edit a document, but instead takes you to a realistically recreated version of the Google website and asks you to login. If you do what this sketchy site says and enter your login info, you will have just given away your Google account information to the scammers behind this scam, providing them with free access to all information stored and associated with your account.
A good way to safeguard against this scam is to be cautious about clicking on Google Doc links unless you know who exactly is sending it. It would be unusual for a friend or business to send a link such as this without including something to indicate what the document is for. If you do click on the document link, you could check the URL or login page for any potential misspellings or signs of something looking weird.
Most importantly, make sure you are always using some form of two-factor authentication* as a safeguard for your account, so even if you do fall victim of a phishing scam, the scammer would still need the code or some other verification to get into your account.
A good rule of thumb to remember with these scams is that if you aren’t familiar with who sent you a message or something feels off, be hesitant before you click on the link. If you need help with setting up two-factor authentication, please visit me at the shop for assistance!
*Two-factor authentication is a 2-step method of keeping your accounts secure. The first factor is your password. The second factor would be a text, email or phone call to you with a code that must also be entered in order to complete the login.

Remote Access Software
By Bryan Stetser
As we move past the craze of the 2020 pandemic, it is still important to bring up a powerful tool that continues to see common use: Remote Access software. TeamViewer, Anydesk, and RemotePC (to name a few) are tools which can allow one to remotely access another computer via means of an Internet connection.
When used properly, said software can allow for users to access and work on a device that might not be easily accessible, or used if one wanted to quickly check up on another computer without having to be physically sitting at the computer. Both computers need to have the software installed and be running it.
There are various jobs that can be accomplished through these programs, allowing for the possibility to partially or fully work remotely. Remote access software can be a powerful productivity tool for legitimate purposes, and it isn’t dangerous on its own.
It can, however present some hefty problems for casual users and some things should be taken into consideration before deciding to use it. One of the biggest concerns is that scammers tend to use this software a lot.
Once a connection is open between yours and a remote computer, the user of the remote computer can see everything on your computer (private information, account data and passwords) and operate it just as if they were sitting at your computer (including logging into any accounts where you have saved passwords for easier access).
While you always have to place a certain amount of faith in anyone who works on your computer, it can be especially risky to entrust someone else to remote into your device, especially when it’s someone you don’t know.
A good rule of thumb is that if you run into a virus or site that starts spewing up a bunch of stuff asking you to call a phone number and the first thing they do is ask you is to download some remote access software, unless you know for sure that you are talking with a legitimate company representative or support person, and not some foreign scammers trying to make a quick buck, DON’T DO IT!
Remote access software can be a great tool to accomplish tasks; whether it is used for good or evil is entirely dependent on who is using it. Be careful!

Virtual Private Networks
By Bryan Stetser
While the internet continues to expand and work its way into our daily lives, it is still important to be mindful of how dangerous it can be. Internet security has always been a roller coaster of effectiveness. We’ve long accepted the importance of strong passwords and Anti Virus software. Another useful tool for added security and privacy is a Virtual Private Network or VPN. They are easy to set up and use.
There are a few different reasons people choose to use VPNs. The one situation where I feel using a VPN is essential is when you are using unsecured public WiFi. Unlike your home WiFi which should always require a password to access, public WiFi has no such built in security and as such, your personal data is literally up for grabs.
A VPN is software which encrypts (scrambles) your data then sends it through a private server and delivers it safely to it’s destination. It also masks the IP address of your device and hides your location. Even if intercepted by someone unscrupulous, they would not be able to decipher your data. If you have to transmit any sensitive data over public WiFi, always use a VPN.
There are other reasons people choose to use VPNs and those are usually for privacy. Your internet provider has the ability to see all data sent and received through their servers. While your provider will know you are using a VPN, they will not be able to see what you’re looking at or doing online. VPNs also prevent websites from tracking you.
Sometimes, websites have blocks in place as well as content region blocks. These prevent certain visitors from accessing sites. If you’ve ever been on Facebook, clicked on a video to watch and received notification that your access is not granted for your country, that is a content region block. It may be a site in Europe that doesn’t allow American access. With a VPN, you would be able to use a setting to send your data through a non American server and then see the video.
While VPNs are legal in many places, you should check before setting one up to make sure your country hasn’t outlawed the use of them.
There are many free VPNs available, but as with anything else, you get what you pay for. When choosing a VPN, more expensive doesn’t necessarily mean better. Read reviews, compare pricing, ask friends and family what they use.
Some sites and services might have VPN detection systems in place, and not allow access to VPN users. VPNs can also slow down your access. Even with the downsides, if you feel like you want your internet to have an added layer of security and protect your privacy, consider using a VPN.

Free Productivity Software
By Bryan Stetser
If there is one use that we tend to associate with computers, work usually comes to mind. In the past, programs like Microsoft WORD and WordPad proved rather important when it came to writing up polished looking documents for work and business. However in recent years, things have begun to change with various products starting to move from a model where you pay once and use it for as long as you want, to a recurring subscription service that you have to constantly shell out money for.
WordPad (which had always been bundled as part of Windows) is going through the process of being discontinued by Microsoft; forcing users to seek out alternatives. If you are interested in looking for alternatives but don’t want to fork out money for an MSOffice license, why not try out something like WPS Office or LibreOffice?
WPS Office and LibreOffice are completely free and replicate the MSOffice experience nicely.
While WPS Office is free, since it is developed by a company, there is also a paid Pro version for around 5 to 6 dollars monthly with some added extras like PDF editing and multi device support, as well as getting plenty of consistent updates.
LibreOffice is also 100% free and open source, meaning not only you can download it and use it without needing to pay a cent, but there is an open community of people working to improve and expand on the product, although updates might not always be as consistent as WPS Office.
Both applications offer their own versions of WORD, Excel, and PowerPoint as well as support for PDF editing. WPS Office is available for Windows, Mac, Linux, Android and iOS. LibreOffice is available for Windows, Mac and Linux.
These applications aim for as much compatibility with MSOffice documents as possible, but there might be some cases where a WORD document could look different in WPS Office or LibreOffice, though it’ll likely depend on what kind of documents you write. While they do share plenty of similarities, it is noted to some that the WPS Office’s UI might be more user friendly to newcomers compared to LibreOffice, but since both apps are free, it doesn’t hurt to try and see which you prefer. If you feel as though you’d want to try something different from MSOffice and save money, try out WPS Office and LibreOffice. I think you’ll be pleased at how much is included in these programs and find they will handle your workload just as well as their more expensive counterpart.
If you find one of these alternatives a great money saving option for your needs, consider supporting them by purchasing the Pro version of WPS Office or donating to LibreOffice.
Below are links to visit each site.
WPS Office https://www.wps.com/
LibreOffice https://www.libreoffice.org/discover/libreoffice/



What is RAM?
By Bryan Stetser
Computers continue to get more complex and powerful with the various parts inside playing important roles in daily computing. While back in the day you could pick up a regular old computer (nothing fancy by today’s standards) and do your business work, these days it’s important to know the terms that refer to the parts of your computer in order to make well-informed choices when purchasing your system.
Today we will be going over two parts of the computer which often confuse consumers; the RAM and HDD.
RAM is Random Access Memory, (long flat circuit boards inside your computer that typically plug into the motherboard, although there is also RAM soldered directly onto the motherboard). RAM can be compared to your brains’ short-term memory function. It functions as a method of temporarily storing data from applications you run, essentially requesting that data to be allocated so your application will properly function. RAM is also volatile; if you close the application or the computer shuts down, the RAM gets emptied.
The amount of RAM you’ll need for daily applications might vary from case to case Basic laptops with 4gbs of RAM minimum is generally suitable for the casual user browsing the net, streaming shows or working on Word documents, spreadsheets and the like, although I’d recommend 8gb if your budget allows and you plan on doing more serious work like Photoshop. 16gb of RAM would be recommended to work comfortably doing video editing with a program like Adobe Premiere, or you have some interest in modern gaming. Any less and you might run into slowdown issues if not outright crashes from your device running out of memory. The amount of RAM you can use does go higher than 16gbs, but how much you need ultimately depends on what your workload is.
Drive storage is permanent storage and where your important files like pictures, videos, documents, and applications reside, essentially functioning like the long term memory functions of your brain, remembering important things that can be recalled later down the line. Because it is required to store files for a long period of time, it is considered non volatile as it can retain data even when the computer is turned off. Because permanent data storage requires a lot of space, these drives must hold more data compared to RAM, potentially being able to hold up to Terabytes of storage for long term preservation. How much drive storage you need will depend on your personal habits. Someone who uses the internet for casual browsing and chatting with friends might not need as much storage as someone who routinely downloads or stores lots of photos, videos, documents, apps, etc on their device. Drive storage comes in different forms like HDD (Hard Disk Drives which stores data on a magnetic disk accessed by platters) and SSD (Solid State Drives which use flash memory like RAM does, but in a non volatile way thus allowing for long term storage.)
While it helps to know the difference between the two, it also helps to keep in mind that technology is constantly advancing. Even if you can get away with running Windows 11 with 4gb of RAM and 128gb of storage, you might run into problems as newer versions of Windows and newer versions of software may require more RAM and files may likewise increase in size.
If you feel like your device might be lacking in storage space or RAM, look for options to physically improve and increase the longetivity of your current device or even plan future device purchases with your workflow in mind.
As always, I welcome you to visit me at the shop to talk about what options you might wish to consider!


How to Choose a Flash Drive for Data Storage
By Bryan Stetser
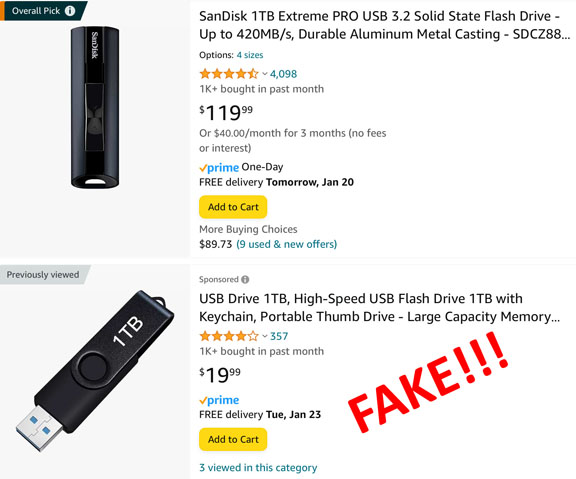
With technology continuing to advance over the years, it has become much easier, cheaper and more convenient to backup and store your data for safe-keeping. Storage options have evolved from tape to floppy disks to CD-ROMS and finally arriving at USB Flash Drives and SD Cards. Like a double edged sword though, there has also been a rise in fake storage devices. How can you tell the difference between legitimate and fake devices, though? My article today will focus on USB Flash Drives since they tend to be the most popular portable devices for data storage.
When shopping for Flash Drives, you really want to pay attention to manufacturer, capacity and price. A good quality, reliable Flash Drive will not be cheap.
Fake storage devices always appear to be good value at a low price. It can be confusing when you look at a list of drives and you may wonder why one company manufactures 1TB drives which cost well over $100 while another company offers 2TB drives for around $30.
It is difficult to produce reliable high capacity flash drives. 1TB is the limit you’d want to consider, assuming it’s from a legitimate manufacturer. You can expect to pay no less than $100 for a reliable 1TB device. Do not consider 2TB drives; reliable manufactures do not produce anything higher than 1TB for regular consumers.
How do fake drives appear to be high capacity? They are actually repurposed low capacity flash drives (usually 32 or 64GB) which have their firmware programmed in a way to report more storage than they actually have when you plug them into your computer. When you start moving data onto the fake drive and it starts running low on storage, it will just quietly write over your data. Say you save 30GB of videos to your drive, and then add another 50GB of videos later. All your videos will appear to be on the drive, but you won’t find out until you go to open your videos and find them corrupted and unable to be opened.
Even if they cost a bit more, I will always recommend you stick to reputable brands of portable storage devices (no matter how big or small the capacity) to ensure you aren’t getting scammed out of your money and lose your valuable data. Samsung, Western Digital, SanDisk, Corsair, Kingston, and Lexar are a few to use.
As the old saying goes, better to be safe than sorry, especially when it comes to data storage. If you need help with your portable data storage, please stop by my shop and let me assist you!


Facebook Video Scams
by Guest Contributor
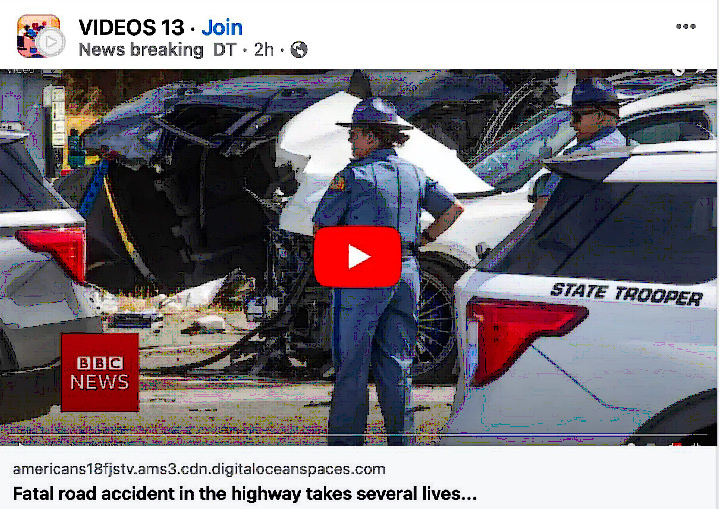
Recently, a friend of mine in Hawaii posted a video of a car accident on her timeline and I received a notification of the post with her commenting “I can’t believe he is gone: I’m gonna miss him so much”. I immediately recognized this as not being her own post, because these posts have been around for awhile. I texted her to let her know; she said she’d been hearing from lots of friends (because the post had been replicated several times, tagging more friends each time.) She was unable to see it on her timeline to delete it. She had gotten an email earlier from Facebook saying someone from California had logged into her account, so she promptly changed her password. It seems someone was able to get her password somehow. These scams are also occurring on cloned accounts as well.
Scammers recognize people’s empathy over a friends loss as well as wanting more information on who your friend lost and how. They also know you’d not question whether or not the post is legitimate, since it was posted by a friend, someone you trust. The “video” displays a thumbnail image which looks like the scene of a tragedy. There are other variations of these posts as well, but they all have some shock value.
There is NO video. Clicking to play what you believe is a video will take you to the second phase of the scam, being taken to the actual scam website where you can be tricked into different ways of providing personal info or lured into downloading malicious viruses or software.
The takeaway here: if you see your friend posting a shocking video, check with your friend first; don’t click on it!

Is Your Internet Fast Enough?
By Bryan Stetser
January 7, 2024 – While the digital age keeps advancing and improving, so does the need to be constantly connected online. Whether you use the internet for email, banking, watching videos, gaming, to purchase items online, or even indulging in personal hobbies, more people use the internet now than ever.
Having good internet can be a different story though. Some are lucky enough to live in an area with decent to good wired fiber internet, but not everyone has this option. Some people, like those who live in more rural areas, might only have access to satellite as means to connect to the internet, which works at a pretty minimum level. While regular satellite internet options might be passable/below average depending on what you need, if you require something faster to handle situations like online web calls, gaming, streaming, etc., it might be worth looking into Starlink which uses low-orbit satellites.
Recently I upgraded to Starlink from wireless line-of-sight internet. The speed differences are like night and day. While it costs more, if you tend to use the internet for services that require fast consistent speeds, it might be worth checking out services like Starlink.
Prices for Starlink are not cheap. Equipment cost is currently $599 for the dual band modem, dish, and cabling. There is no option to rent this equipment. The cost of monthly service for the standard plan starts at $120 per month with no contracts and 30 days to trial out the service.
In order to obtain service from Starlink, a clear, unobstructed (no trees or buildings in the way) view of the sky is necessary. The dish itself angles about 30° upwards and seems to remain north facing at my home.
There is a Starlink app you can download to help you determine if the service is available in your area and how well it will work for you. It’s very easy to use and if one area of your property doesn’t work, you can repeat the process in different locations. There are several mounting options as well; I started with my dish out in the yard and later had it mounted on top of my dog kennel. The dish also will heat when it detects snow, so you don’t have to go out in the cold to sweep off snow.
The setup itself was easy and straightforward. You get to pick your own modem name and password and the modem boots pretty quickly compared to other modems I’ve used. It defaulted to single band (5GHz) on setup and in order to access 2.4GHz, there is an option in the app to configure that band as well.
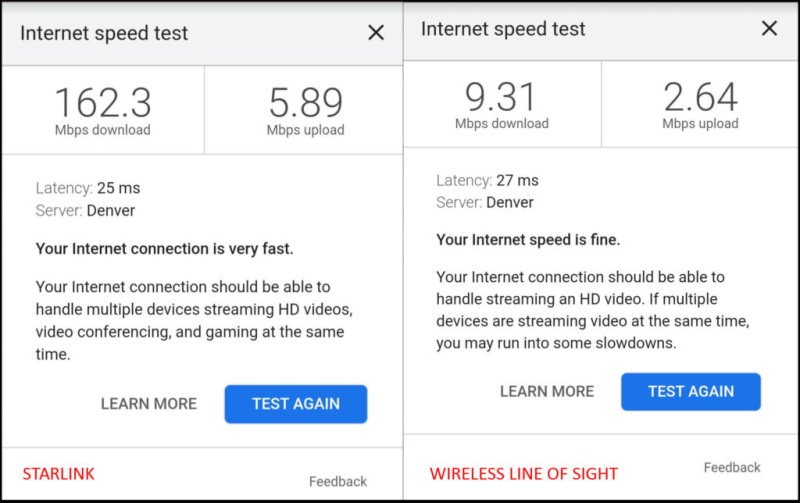
I will mention that while the speed of Starlink is very impressive, it does not constantly maintain the exact same download or upload speeds. The actual speed is somewhat variable but is always extremely faster than my old service. I have noticed brief periods where it appears to drop service momentarily as well, but recovers quickly.
My biggest disappointment is the modem does not have an Ethernet port, so out of the box I was unable to hook up devices that require an Ethernet connection (printer, VOIP phone, and a Smart Hub). Starlink does sell an Ethernet adapter ($25) which will provide a single Ethernet port and from there I connected a router to increase port availability. The router cost about $60.
I have been using Starlink for about 3 months now and am very satisfied with its performance. Below is a comparison of speeds between Starlink (left) and my wireless line of sight at the shop (right).

PUT SOME PEP IN YOUR COMPUTER’S STEP
By Bryan Stetser

December 30, 2023. As time marches on, it is inevitable the laptops and computers we purchased years ago might start slowing down or having various issues. While there can be plenty of variables for why an old computer might start slowing down (one example could be running out of storage space), a reasonably common bottleneck could likely be the type of storage drive your device uses.
Older laptops and desktops tend to use HDDs (Hard Disk Drives) to not only handle storage, but also boot Windows. While they are good for long term storage, these drives can eventually start slowing down after years of constant use due to their moving parts. Assuming there are no other issues such as viruses, malware, or corrupted boot files, an aging drive can increase boot times from seconds to even minutes on start up!
If your computer is taking a long time to boot, stop by the shop and I’ll evaluate what could be the cause. If it’s a drive that is worn from time, you might wish to consider upgrading to a Solid State Drive (or SSD for short). Not only do these drives contain no moving parts (meaning a slight bump won’t potentially cause damage and render the drive unreadable), but they are much faster, too. While larger capacity hard disk drives can be cheaper replacements, SSDs have gone down in pricing enough to be really affordable, and most laptops and desktops can accept SSD replacements.
With a bit of technical know-how, you could replace your old hard drive with a fresh new SSD!
If your laptop or desktop starts taking forever to boot and you notice your hard drive sounding like it’s working even when you’re not actively using your computer, a speedy SSD might be the upgrade for you. If you’d rather not do the replacement yourself, Computers & More of Raton can help you find the right SSD for your needs and do the work for you!

Beware – Hackers Pretend to be a Friend Asking for Help
By Bryan Stetser
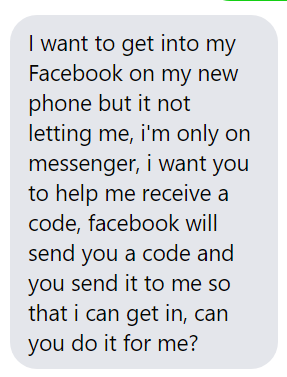
If someone messages you something similar to this, asking for a code to be sent to your phone or email on their behalf, please don’t do it. This is not your friend asking for help, it’s a hacker. A friend of ours has lost access and control of her FB account because someone unknowingly agreed to help thinking it was her asking. These types of messages are not from the account owner.
The Importance of Surge Protectors
By Bryan Stetser

If you have a computer, laptop, or any kind of electronics plugged into an outlet, make sure you are using a fresh surge protector or an Uninterruptable Power Supply (UPS) to safeguard your tech. Surge protectors might protect your devices at first, but they can lose effectiveness over time, especially with lightning strikes. Uninterruptable Power Supplies also function like portable power banks, giving you extra time to shut off your devices safely before the power runs out. Thunderstorms and power blackouts can be especially dangerous if you fail to prep for them. When they happen, your computer could suddenly shut off, risking any unsaved data you had open, or in an even worse case scenario, you risk potential hardware failure from the storm frying your device.
If your computer or laptop isn’t booting after a thunderstorm anymore, bring it down to Computers and More of Raton for an evaluation! If it’s fried, it might still be possible for me to retrieve your data off the drives.

Windows Security Pop Up Scam Ad
By Bryan Stetser
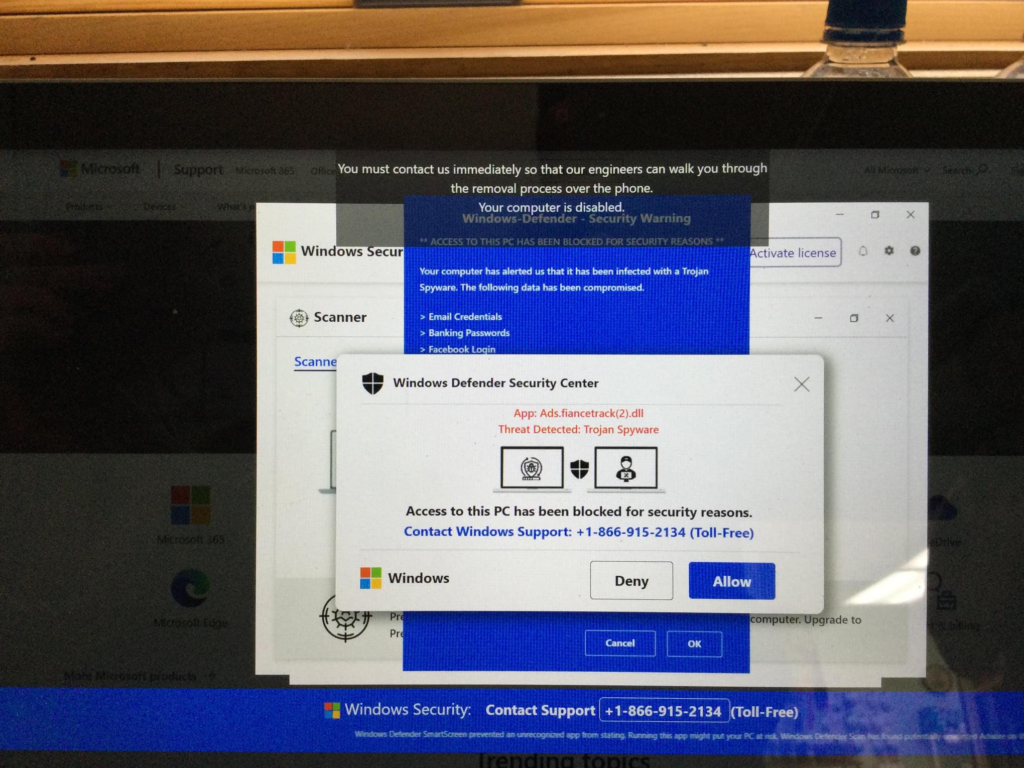
This window opened on my mother’s pc while she was playing a game on Facebook. While you are on the internet, make sure you are aware of the potential dangers of scam ads that try to pretend you PC is in danger and ask you to install or contact throwaway phone numbers. There will be moments where your browser will sometimes be redirected to a fake security warning site that talks about your PC being compromised. If you happen to see something like that while browsing, try to close out of the browser if possible and run Windows Defender, Malwarebytes, or whatever anti-virus software you have on your computer. Under no circumstances should you click on any download links on suspicious pages or call questionable phone numbers for tech support, as they rely on the user being scared enough into doing what they say. Make sure you also pick up ad blocking software like ublock origin, a tool that can block out most ads on the web keeping you safe. Remember to be extremely cautious about letting people remote into your computers as well, as it can be a sure-fire way to lead to questionable people getting access to your private information. Windows Defender will never disable your computer or force you to call a phone number and ask to install remote software to get your computer back into a working state.

Windows 11 and The Future of Computers
By Bryan Stetser

As time marches on, technology will always advance and improve over what we had long ago, such is the case for computers. Microsoft has always been at the forefront of computing, even with it’s competition such as Mac and Linux. However, with Windows 11 coming out very soon, Microsoft has decided to implement a rather strange upgrade policy if you want to upgrade in the first place, by requiring TPM 2.0 support. It is normal for newer operating systems to require newer hardware to run, but Windows 11 is a weird case where even some of the newer computers out there don’t have support for it yet, resulting in Microsoft’s checker app saying they can’t upgrade.
If you are curious about what TPM is, it stands for Trusted Platform Module, a form of device encryption to help protect against malicious attacks against said device and is found on your motherboard. There should be a TPM header spot somewhere that you can slot the 2.0 chip into, which I’d personally recommend doing with a chip that not only has the same pin number and layout of the header, but is also from the same brand as well.
It is possible to install Windows 11 without a TPM 2.0 chip setup, however you’ll be missing out on vital updates and might be at risk of encountering issues according to Microsoft.
TPM chip aside, the other major thing to note is that you’ll need a pretty new processor that came out around 2018-2019 (maybe 2017 in some cases) if you want to have one that meets the minimum requirements. Even with the rather high hardware requirements to attempt upgrading in the first place, most people who have tried the new 11 OS consider it to be average enough or slightly worse when compared to windows 10, with the start bar being shifted to the middle, barely any performance improvement, Microsoft’s aggressive pushing for you to use Edge, and a weird blend of trying to revamp the settings and such while still keeping older stuff around like the control panel. Even with Microsoft planning to cut off Windows 10 support on October 14th 2025, you’ll still be able to use your computer like normal, but security updates and support as such won’t be supplied anymore.
Newer hardware or even certain applications might have a cut off point where you’ll have to either upgrade or be forced to use older or sometimes outdated equipment or applications.
If you still want to bite the bullet for now and upgrade anyway, keep in mind that you’ll need to meet the requirements if you want to take full advantage of the system, which might prove to be an
issue if your computer lacks a TPM 2.0 chip or has an older processor. Even if you meet the requirements and upgrade, you’ll only get a 10 day grace period to test the OS and see if you like it
before Windows auto deletes your Windows 10 files permanently to clear up space. I’d personally recommend waiting awhile before upgrading/buying a new PC, since TPM 2.0 support still seems to be confusing a lot of people with some computers having it and some of them lacking it. Maybe Microsoft will think about lowering some of the requirements later down the line, but on the off chance they decide to stick to it, there will still be newer computers around with Windows 11 available for purchase if you don’t want to mess around with your current computer to get TPM 2.0 setup.
There are also plenty of alternative options if you don’t want to deal with the newer OS’s anymore, such as the Raspberry Pi 4, a smaller computer running the Linux operating system that’s affordable, easy to setup, has no moving parts. You don’t have to worry about ever upgrading hardware or strict hardware requirements or lack of support. Stop by the shop to see what a Raspberry pi is!









